First thing first:
They don't learn from your preferences.
They don't grow with you.
Every conversation starts from zero. That brilliant solution you worked out together yesterday? Gone. Your coding style preferences? Never existed. It's like having a colleague with no memory who reads the same Wikipedia snapshot from 2023 every morning.
This is the gap every AI project tries to bridge. The spoiler?
They're all running on something called ⭐ Workflow ⭐ — structured chains of steps that actually work. We'll get to that more clearly in the whole deep dive series, starting with "Prompting" in this article.
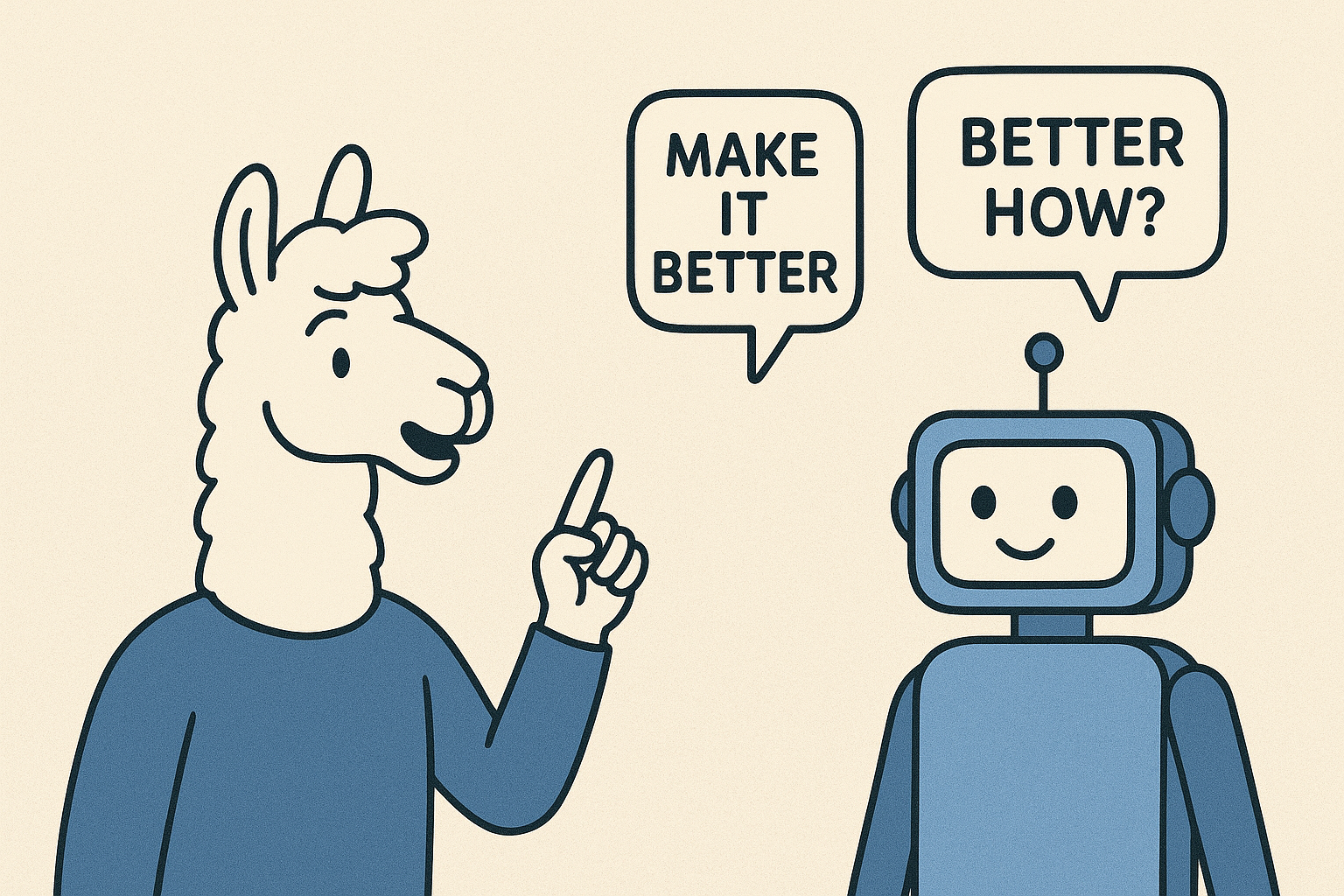
The Problem: Translation Lost
Ever tried explaining something to someone and they completely misunderstood you? Now imagine that someone is an AI that takes everything literally. That's prompting in a nutshell.
You ask ChatGPT to "improve" your code, and it rewrites the entire thing in a completely different style. You tell Claude to be "concise" and it gives you one-word answers. When you ask an LLM to "make it better", what exactly does "better" mean? More concise? More detailed? More formal?
In this deep dive, we're tackling the foundation of every LLM interaction: getting these models to actually understand what you want.
All the code examples in this article use LiteLLM for unified API calls and OpenRouter for accessing various models (including free ones). This keeps the examples practical and reproducible without requiring expensive API keys.
All is backed with uv — a python package manager. Go check the README file if you'd like to run scripts by yourself, remember to get your OPENROUTER_API_KEY in advance!
1. The Intent Gap: What You Think vs What You Say
Here's a fun experiment. Ask any LLM to "analyze this data" without providing context. Watch it struggle. Now ask a colleague the same thing — they'll immediately ask "what kind of analysis?" or "what are you looking for?". That's the intent gap right there.
Real Examples of Prompt Failures
The classic one? "Make this function better":
def calculate(x, y):
return x * y + 10 + 10
- 👨🦱 What you meant: "Optimize for performance"
- 🤖 What the LLM heard: "Rewrite everything with type hints, docstrings, and error handling"
The LLM might give you a 50-line class with dependency injection when all you wanted was a faster multiplication algorithm.
Why Context Matters more than You Think:
LLMs are like contractors showing up to a job site with no blueprints. Sure, they have all the tools, but without context, they're just guessing what you want built.
The Hidden Assumptions in Your Requests:
When you say "summarize this", you're assuming the model knows:
- How long the summary should be
- Who the audience is
- What details matter most
- Whether to preserve technical accuracy or prioritize clarity
Spoiler: It doesn't know any of that.
Instead, it makes its best guess — which often means hallucinating details or asking clarifying questions when you're using a reasoning model.
2. Prompt Engineering Fundamentals
Let's cut through the fluff. Here are the patterns that actually work.
System vs User Prompts: Who Does What?
Think of system prompts as the LLM's job description. User prompts are the specific tasks. Mix them up, and you get a confused AI trying to be helpful in all the wrong ways.
from litellm import completion
from dotenv import load_dotenv
from os import getenv
# Load environment variables
load_dotenv()
# Bad: Everything crammed into one message
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[{
"role": "user",
"content": "You are a SQL expert. Fix this query: SELECT * FROM users WHERE age = '25'"
}]
)
# Good: Clear separation of concerns
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{
"role": "system",
"content": "You are a SQL optimization expert. Focus on performance and security."
},
{
"role": "user",
"content": "Fix this query: SELECT * FROM users WHERE age = '25'"
}
]
)
print(response["choices"][0]["message"]["content"])
# Output: "SELECT * FROM users WHERE age = 25 -- Fixed: removed quotes from numeric comparison"
Run this example yourself 🔧
Script:
1_system_vs_user_prompts.py
Command:
uv run 1_system_vs_user_prompts.pyExpected Output:
System vs User Prompts Demo
=== BAD APPROACH ===
Query fix (bad approach):
[94m**Short answer**
```sql
-- If `age` is a numeric (e.g. INT, SMALLINT, etc.):
SELECT *
FROM users
WHERE age = 25;
```
**Why that fixes the query**
| Problem in the original | What it does | What to change | Reason |
|---------------------------|--------------|----------------|--------|
| `age = '25'` (string literal) | Imposes an implicit cast that can degrade performance, and may even lock the column unnecessarily. | Use a numeric literal (`25`) or CAST it explicitly. | Matching the data type keeps the column indexed and avoids implicit conversions. |
| `SELECT *` | Pulls every column, which can mean more I/O, memory pressure, and network traffic than necessary. | List only the columns that you actually need (e.g. `id, name, email`). | Minimises data transfer and makes the intent clear to the DB engine. |
| No parameterization | If you’re embedding this query in application code, you risk SQL‑Injection. | Use placeholders (`?`, `$1`, etc.) depending on your driver. | Defensive programming – safer and more maintainable. |
---
### Full example with good practices
```sql
-- Example with a SELECT list and a prepared‑statement placeholder
SELECT id, name, email
FROM users
WHERE age = $1; -- or ? / @age depending on your DB client
```
```postgresql
-- (PostgreSQL example)
PREPARE get_users_by_age(integer) AS
SELECT id, name, email
FROM users
WHERE age = $1;
-- Execute with the numeric age value
EXECUTE get_users_by_age(25);
```
---
### If you really *must* keep `age` as a string
If your schema is weird and `age` is stored as a text column, you can still write the query in a slightly cleaner way:
```sql
SELECT *
FROM users
WHERE age = CAST('25' AS text); -- or just keep '25' but avoid the extra quotes
```
But the preferred course of action is to store numeric data in numeric columns.
---
### Quick checklist
1. **Match data types** – no unnecessary quotes around numeric constants.
2. **Select only needed columns** – replace `*` with an explicit list.
3. **Use parameters** – if the value comes from user input or app code.
4. **Test** – verify that the result set is still what you expect after the change.
After applying the above, your query should run more efficiently and be safer to maintain. Happy querying![0m
==================================================
=== GOOD APPROACH ===
Query fix (good approach):
[94mBelow is a “fix‑up” that addresses the two most important goals for a production‑grade query in a user‑table: **security** (avoid injection) and **performance** (use the right data types, indexes and only the columns you need).
---
## 1. The original query
```sql
SELECT * FROM users WHERE age = '25';
```
### Problems
| Issue | What it does | Why it hurts |
|-------|--------------|--------------|
| `age = '25'` | Treats the literal as a **string** | If `age` is an `INT` column the DB will cast the string to a number, wasting CPU ops. |
| `SELECT *` | Returns every column | Unnecessary I/O, larger result set, more bandwidth, and increases the cost of any covered index. |
| No parameterisation | If this statement is built with string concatenation, it’s vulnerable to SQL‑Injection. | An attacker could inject arbitrary SQL if any part of the query were derived from user input. |
| No index hint | If the `age` column isn’t indexed, the query will scan the whole table. | Poor perf, especially on large tables. |
---
## 2. A better rewrite
### a. Use the correct data type
```sql
SELECT id, name, email, age -- <‑ list only what you really need
FROM users
WHERE age = 25; -- <‑ integer literal, no quotes
```
**Why?**
*No implicit casting* – the engine reads the integer column straight from the index or data pages, which is faster.
### b. Create an index (once)
```sql
CREATE INDEX idx_users_age ON users(age);
```
An index on the filter column lets the optimiser perform an index lookup instead of a full table scan.
### c. Parameterise in your application
> **Never concatenate user data into the SQL string.**
> Bind a value, and let the driver handle quoting, escaping and type conversion.
**Example in PHP with PDO**
```php
$age = 25; // or whatever comes from user input after validating it’s an int
$sql = 'SELECT id, name, email, age FROM users WHERE age = :age';
$stmt = $pdo->prepare($sql);
$stmt->bindValue(':age', $age, PDO::PARAM_INT);
$stmt->execute();
$rows = $stmt->fetchAll(PDO::FETCH_ASSOC);
```
**Example in Python with `psycopg2` (PostgreSQL)**
```python
age = 25
cur.execute("""
SELECT id, name, email, age
FROM users
WHERE age = %s
""", (age,))
rows = cur.fetchall()
```
---
## 3. Optional enhancements
| Enhancement | When to use | Benefit |
|-------------|-------------|---------|
| **Covering index** | `SELECT age, id, name, email FROM users WHERE age = 25;` with `CREATE INDEX idx_users_age_covering ON users(age, id, name, email)` | The query can be satisfied entirely from the index, no data‑page fetches. |
| **Stats update** | After heavy inserts/updates | Keeps the optimiser's stats accurate so it can pick the index‑lookup plan. |
| **Query profiling** | When you notice unexpected slowdowns | Tools like `EXPLAIN ANALYZE` (Postgres), `EXPLAIN PLAN` (Oracle) or `SHOW PROFILE` (MySQL) will help you confirm the planner is following the index. |
---
## 4. Summary checklist
- **Schema** – ensure `age` is of the correct type (INT, SMALLINT, etc.).
- **Index** – `CREATE INDEX idx_users_age ON users(age);`
- **SELECT** – list only the columns you need.
- **Literal** – use a numeric literal (`25`) not a quoted string.
- **Parameterise** – never concatenate user input; use prepared statements.
By applying all four steps you’ll have a query that is **completely safe from injection**, uses the _right_ data type, reads from an index, and returns no more data than required – the triple‑win formula for performance, security, and maintainability.[0m
=== SYSTEM PROMPT COMPARISON ===
--- Generic System Prompt ---
[94mTo optimize the given query, we can apply several strategies:
1. **Use Explicit JOINs**: Instead of using the implicit join syntax (`FROM orders o, users u WHERE o.user_id = u.id`), use explicit JOINs. This makes the query easier to read and understand, and it can also improve performance by allowing the database to optimize the join order.
2. **Use Indexes**: Ensure that the columns used in the `WHERE` and `JOIN` clauses are indexed. In this case, we should create indexes on `orders.user_id` and `users.id`. This can significantly speed up the query by allowing the database to quickly locate the matching rows.
3. **Use Efficient JOIN Order**: The order in which we join tables can affect performance. In this case, since we're filtering by `o.total > 1000`, it might be more efficient to join `orders` with `users` first, and then filter the results. However, the optimal join order depends on the specific database system and the data distribution.
4. **Limit the Columns Retrieved**: Instead of selecting all columns (`SELECT *`), specify only the columns that are needed. This can reduce the amount of data being transferred and processed, which can improve performance.
Here's the optimized query:
```sql
SELECT o.*, u.*
FROM orders o
JOIN users u ON o.user_id = u.id
WHERE o.total > 1000;
```
Or, if you only need specific columns:
```sql
SELECT o.order_id, o.total, u.name, u.email
FROM orders o
JOIN users u ON o.user_id = u.id
WHERE o.total > 1000;
```
**Additional Tips:**
- Regularly analyze your database's query performance using tools like EXPLAIN or EXPLAIN ANALYZE to identify bottlenecks.
- Consider partitioning large tables to improve query performance.
- Keep your database indexes up-to-date and ensure they are properly maintained.
- Regularly review and optimize your database schema to ensure it is optimized for your use case.[0m
==================================================
--- Specific System Prompt ---
[94mTo optimize this query, we'll consider several factors, including indexing, joining, and filtering. Here's an optimized version:
```sql
-- Create indexes on columns used in WHERE and JOIN clauses
CREATE INDEX idx_orders_user_id ON orders (user_id);
CREATE INDEX idx_users_id ON users (id);
-- Optimize the query
SELECT o.*, u.*
FROM orders o
INNER JOIN users u ON o.user_id = u.id
WHERE o.total > 1000;
```
Here's what changed:
1. **Indexing**: We created indexes on the `user_id` column in the `orders` table and the `id` column in the `users` table. This will significantly speed up the join operation, as the database can quickly locate the matching rows in the `users` table.
2. **Inner join**: We replaced the implicit join syntax (`FROM orders o, users u WHERE o.user_id = u.id`) with an explicit inner join (`INNER JOIN users u ON o.user_id = u.id`). This makes the query easier to read and understand.
3. **Removed unnecessary columns**: We removed the `SELECT *` and instead specified the columns we actually need (`o.*` and `u.*`). This reduces the amount of data being transferred and processed, which can improve performance.
Additional suggestions:
* If you're using a database management system that supports it (e.g., PostgreSQL, MySQL 8.0+), consider using a **covering index** on the `orders` table to include the `total` column. This can further improve performance by reducing the need for a table scan.
* If the `orders` table is very large, consider using a **partitioning** strategy to split the data into smaller, more manageable chunks. This can improve query performance and reduce the load on the database.
* If the `users` table is very large, consider using a **materialized view** or a **derived table** to reduce the number of joins and improve performance.
Example use case:
Suppose you have a large e-commerce database with millions of orders and users. You want to retrieve all orders with a total value greater than $1000, along with the corresponding user information. The optimized query above will efficiently retrieve the required data, leveraging indexes and a proper join strategy to minimize the load on the database.[0m
==================================================
--- Context-Rich System Prompt ---
[94m**Optimizing the Query**
The given query is a simple join between two tables, `orders` and `users`, on the condition that the `user_id` in `orders` matches the `id` in `users`. The query also filters the results to only include orders with a total value greater than 1000.
**Original Query**
```sql
SELECT *
FROM orders o, users u
WHERE o.user_id = u.id AND o.total > 1000;
```
**Optimized Query**
To optimize this query, we can use an `INNER JOIN` instead of the implicit join syntax. This makes the query more readable and maintainable. We can also add an index on the `user_id` column in the `orders` table to improve the join performance.
```sql
-- Create an index on user_id in orders table
CREATE INDEX idx_orders_user_id ON orders (user_id);
-- Optimized query
SELECT o.*, u.*
FROM orders o
INNER JOIN users u ON o.user_id = u.id
WHERE o.total > 1000;
```
**Explanation**
1. We create an index on the `user_id` column in the `orders` table to speed up the join operation.
2. We use an `INNER JOIN` to explicitly specify the join condition, making the query more readable and maintainable.
3. We select only the columns we need (`o.*` and `u.*`) to reduce the amount of data being transferred and processed.
**Additional Recommendations**
* Consider adding an index on the `total` column in the `orders` table to improve the filtering performance.
* If the `orders` table is very large, consider using a covering index on the `user_id` and `total` columns to reduce the number of rows being scanned.
* If the query is still performing poorly, consider partitioning the `orders` table by date or other relevant columns to reduce the amount of data being scanned.
**Example Use Case**
Suppose we have the following data in the `orders` and `users` tables:
`orders` table:
| id | user_id | total |
| --- | --- | --- |
| 1 | 1 | 1000 |
| 2 | 1 | 2000 |
| 3 | 2 | 500 |
| 4 | 3 | 1500 |
`users` table:
| id | name |
| --- | --- |
| 1 | John |
| 2 | Jane |
| 3 | Bob |
The optimized query will return the following result:
| id | user_id | total | name |
| --- | --- | --- | --- |
| 1 | 1 | 1000 | John |
| 2 | 1 | 2000 | John |
| 4 | 3 | 1500 | Bob |[0m
==================================================
The Power of Few-Shot Learning
Want the LLM to follow a specific pattern? Show it examples. It's like training a new developer — show them how it's done, not just what to do.
def extract_sql_from_text(user_query: str) -> str:
"""Extract SQL from natural language using few-shot examples"""
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{"role": "system", "content": "Extract SQL queries from natural language. Return only valid SQL."},
# Few-shot examples
{"role": "user", "content": "Show me all users from Texas"},
{"role": "assistant", "content": "SELECT * FROM users WHERE state = 'TX';"},
{"role": "user", "content": "Count orders from last month"},
{
"role": "assistant",
"content": "SELECT COUNT(*) FROM orders WHERE date >= DATE_SUB(CURDATE(), INTERVAL 1 MONTH);"
},
# Actual query
{"role": "user", "content": user_query}
]
)
return response["choices"][0]["message"]["content"]
# Now it knows the pattern
print(extract_sql_from_text("Find customers who spent over 1000"))
# Output: "SELECT * FROM customers WHERE total_spent > 1000;"
Run this example yourself 🔧
Script:
2_few_shot_learning.py
Command:
uv run 2_few_shot_learning.pyExpected Output:
Few-Shot Learning Demo
=== ZERO-SHOT vs FEW-SHOT COMPARISON ===
Query 1: 'Find customers who spent over 1000'
--------------------------------------------------
Zero-shot result:
[94m```sql
SELECT
c.customer_id,
c.customer_name,
SUM(oi.quantity * oi.unit_price) AS total_spent
FROM customers c
JOIN orders o ON c.customer_id = o.customer_id
JOIN order_items oi ON o.order_id = oi.order_id
GROUP BY c.customer_id, c.customer_name
HAVING SUM(oi.quantity * oi.unit_price) > 1000;
```
[0m
Few-shot result:
[94mSELECT customer_id, SUM(amount) AS total_spent
FROM orders
GROUP BY customer_id
HAVING total_spent > 1000;[0m
Advanced few-shot with schema:
[94mHere’s a straightforward query that pulls all customers whose cumulative spending exceeds $1,000:
```sql
SELECT
customer_id,
name,
email,
total_spent,
created_at
FROM
customers
WHERE
total_spent > 1000
ORDER BY
total_spent DESC;
```
- **`total_spent > 1000`** filters for high‑value customers.
- Ordering by `total_spent DESC` shows the biggest spenders first.
Feel free to adjust the columns or add additional filters (e.g., date range, specific departments) as needed.[0m
======================================================================
Query 2: 'Get products that are running low on inventory'
--------------------------------------------------
Zero-shot result:
[94mSELECT * FROM products WHERE inventory_quantity < 10;[0m
Few-shot result:
[94mSELECT * FROM products WHERE quantity <= 10;[0m
Advanced few-shot with schema:
[94m```sql
-- Products that are running low on inventory (threshold: 10 units)
SELECT
product_id,
name,
price,
inventory_count,
category
FROM products
WHERE inventory_count < 10
ORDER BY inventory_count ASC;
```[0m
======================================================================
Query 3: 'Show me orders from the last week that haven't shipped'
--------------------------------------------------
Zero-shot result:
[94m```sql
SELECT *
FROM orders
WHERE order_date >= DATE_SUB(CURRENT_DATE(), INTERVAL 7 DAY)
AND (ship_date IS NULL OR status <> 'shipped');
```[0m
Few-shot result:
[94mSELECT *
FROM orders
WHERE order_date >= DATE_SUB(CURDATE(), INTERVAL 7 DAY)
AND shipped_date IS NULL;[0m
Advanced few-shot with schema:
[94m```sql
-- Orders created in the last 7 days that have not yet shipped
SELECT
order_id,
customer_id,
status,
total,
created_at
FROM
orders
WHERE
created_at >= DATE_SUB(NOW(), INTERVAL 7 DAY) -- last week
AND shipped_at IS NULL -- not shipped yet
ORDER BY
created_at DESC;
```[0m
======================================================================
Query 4: 'List employees who started this month'
--------------------------------------------------
Zero-shot result:
[94m```sql
SELECT *
FROM employees
WHERE YEAR(hire_date) = YEAR(CURRENT_DATE())
AND MONTH(hire_date) = MONTH(CURRENT_DATE());
```[0m
Few-shot result:
[94mSELECT *
FROM employees
WHERE YEAR(start_date) = YEAR(CURDATE())
AND MONTH(start_date) = MONTH(CURDATE());[0m
Advanced few-shot with schema:
[94m```sql
SELECT employee_id, name, department, start_date, salary
FROM employees
WHERE YEAR(start_date) = YEAR(CURDATE())
AND MONTH(start_date) = MONTH(CURDATE());
```[0m
======================================================================
=== PATTERN LEARNING DEMO ===
--- Error Analysis Pattern ---
Input: Query times out
Output:
[94mISSUE: Query timeout | CAUSE: Missing index on frequently filtered column(s) or inefficient join causing full table scans | FIX: Add appropriate indexes (e.g., `CREATE INDEX idx_orders_customer_id ON orders(customer_id)`), rewrite the query to use EXISTS or subqueries, and ensure WHERE clauses use indexed columns.[0m
--- Code Review Pattern ---
Input: SELECT COUNT(*) FROM orders o, users u WHERE o.user_id = u.id
Output:
[94mRATING: 3/5 | ISSUES: 1) Implicit join syntax (comma join) can be confusing and is less explicit than JOIN…ON. 2) COUNT(*) counts all rows, which may double‑count if the join produces duplicate rows (e.g., if a user appears multiple times). 3) No alias for the aggregate, which can make the result set harder to read. 4) No filtering on user status (e.g., active users) – may return counts for inactive users. | IMPROVE: 1) Use explicit JOIN syntax: `FROM orders o JOIN users u ON o.user_id = u.id`. 2) If you only want to count distinct orders, use `COUNT(DISTINCT o.id)` or `COUNT(o.id)` instead of `COUNT(*)`. 3) Alias the aggregate for clarity: `SELECT COUNT(*) AS order_count`. 4) Add any necessary filters, e.g., `WHERE u.active = 1`. 5) If the intent is to count orders per user, consider adding a GROUP BY clause.[0m
Chain-of-Thought: Making the Model Show Its Work
Sometimes you need the LLM to think step-by-step. It's like debugging — you want to see the logic, not just the answer.
def analyze_query_performance(sql_query: str) -> dict:
"""Analyze SQL query with step-by-step reasoning"""
cot_prompt = f"""
Analyze this SQL query step by step:
{sql_query}
Follow these steps:
1. Identify the tables involved
2. Check for missing indexes
3. Spot potential N+1 problems
4. Suggest optimizations
Show your reasoning for each step.
"""
response = completion(
model="openrouter/openai/gpt-oss-20b:free", # Bigger model for complex reasoning
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{
"role": "system",
"content": "You are a database performance expert. Think step-by-step."
},
{"role": "user", "content": cot_prompt}
],
temperature=0.2 # Lower temperature for more focused reasoning
)
return {"analysis": response["choices"][0]["message"]["content"]}
# Example usage
complex_query = """
SELECT u.name, COUNT(o.id) as order_count
FROM users u
LEFT JOIN orders o ON u.id = o.user_id
WHERE u.created_at > '2024-01-01'
GROUP BY u.id
HAVING order_count > 5
"""
result = analyze_query_performance(complex_query)
# Returns detailed step-by-step analysis with reasoning
Run this example yourself 🔧
Script:
3_chain_of_thought.py
Command:
uv run 3_chain_of_thought.pyExpected Output:
Chain-of-Thought Reasoning Demo
=== DIRECT vs CHAIN-OF-THOUGHT COMPARISON ===
--- Direct Approach ---
[94mBelow is a rewrite that cuts the amount of data the engine has to touch, removes the unnecessary `LEFT JOIN`, and uses a pre‑aggregated sub‑query (CTE or derived table).
I’ll also point out the indexes that will make the plan fast.
```sql
/* 1️⃣ Create the indexes that the optimizer will use */
CREATE INDEX idx_users_created_at ON users (created_at);
CREATE INDEX idx_orders_user_id ON orders (user_id);
/* 2️⃣ Pre‑aggregate the orders that actually matter */
WITH order_stats AS (
SELECT
user_id,
COUNT(*) AS order_count,
SUM(total) AS total_spent
FROM orders
GROUP BY user_id
HAVING COUNT(*) > 5 -- only users with >5 orders
)
SELECT
u.name,
os.order_count,
os.total_spent
FROM users u
JOIN order_stats os
ON u.id = os.user_id
WHERE u.created_at > '2024-01-01' -- filter users first
ORDER BY os.total_spent DESC;
```
### Why this is faster
| Original | Optimized | Reason |
|----------|-----------|--------|
| `LEFT JOIN` | `INNER JOIN` | We only need users that have at least 5 orders; the left join would create a row for every user, then the `HAVING` clause would filter it out. |
| `COUNT(o.id)` | `COUNT(*)` | Counting a non‑NULL column forces a null‑check; `COUNT(*)` is cheaper. |
| `GROUP BY u.id` | `GROUP BY u.id, u.name` | Explicitly grouping by the selected non‑aggregated column removes reliance on functional dependency (safer for strict SQL modes). |
| `HAVING order_count > 5` | `HAVING COUNT(*) > 5` | Uses the aggregate directly; no alias lookup. |
| Full join of all orders | Pre‑aggregate in a CTE | The CTE reduces the join to only the users that actually meet the `>5` threshold, cutting the number of rows that the join has to process. |
| Filter on `users.created_at` after the join | Filter before the join | The `WHERE` clause on `users` is applied before the join, so the join sees a smaller set of users. |
### What the execution plan will look like
1. **Scan `users`** – index seek on `created_at` → small set of active users.
2. **Scan `orders`** – index scan on `user_id` → group by `user_id`, keep only those with >5 rows.
3. **Join** – hash or merge join between the two small result sets.
4. **Sort** – order by `total_spent` (already available in the CTE).
If you’re on MySQL 8+, the CTE is materialized once and reused; on older versions you can replace the CTE with a derived table (`JOIN (SELECT …) AS os …`) – the plan is identical.
Feel free to run `EXPLAIN` on the rewritten query to confirm that the indexes are being used and that the join is on the reduced sets.[0m
============================================================
--- Chain-of-Thought Approach ---
[94mBelow is a line‑by‑line walk‑through of the query, followed by a checklist of what to look for and concrete ways to make it faster.
---
## 1. Identify the tables involved
| Alias | Table name | Purpose in the query |
|-------|------------|----------------------|
| `u` | `users` | Source of the customer name and the filter on `created_at`. |
| `o` | `orders` | Source of the order count and the total spent. |
The query pulls one row per user, aggregates all of that user’s orders, and then filters on the aggregate.
---
## 2. Check for missing indexes
| Column | Suggested index | Why it helps |
|--------|-----------------|--------------|
| `users.id` | Primary key (usually already present). | Needed for the join. |
| `users.created_at` | `INDEX (created_at)` or a composite `INDEX (created_at, id)` | The `WHERE` clause filters on this column; an index lets the engine skip all older rows. |
| `orders.user_id` | `INDEX (user_id)` or a composite `INDEX (user_id, total)` | Drives the join and the `GROUP BY`. |
| `orders.total` | Often not needed alone, but part of a covering index. | If you add `total` to the `orders.user_id` index, the engine can read the sum without touching the heap. |
| `orders.id` | Primary key (usually present). | Used by `COUNT(o.id)`; not critical if you switch to `COUNT(*)`. |
**What to do**
1. **Add a composite covering index on `orders(user_id, total)`** – this lets the engine read the user‑id and the total in one go, which is perfect for the aggregation.
2. **Add a composite index on `users(created_at, id)`** – the `created_at` filter and the join key are both covered, so the engine can pull the exact rows it needs without a table scan.
3. **If you’re on MySQL and `ONLY_FULL_GROUP_BY` is enabled, you’ll need `u.name` in the `GROUP BY`** – you can either add it to the group by or use a functional dependency (PostgreSQL does this automatically).
---
## 3. Spot potential N+1 problems
> **N+1** refers to the classic “fetch a list, then fetch each item’s details in a separate query.”
> In this single SQL statement there is no N+1 issue – the whole aggregation is done in one pass.
**However, in application code** you might:
* Run this query to get the list of users, then loop over that list and issue a separate `SELECT * FROM orders WHERE user_id = ?` for each user.
*That would be an N+1 problem.*
*Solution:* Keep the aggregation in the database (as it is now) or use a single `JOIN`/`GROUP BY` query that returns everything you need.
---
## 4. Suggest optimizations
| Problem | Why it hurts | Fix |
|---------|--------------|-----|
| **LEFT JOIN + HAVING > 5** | The `LEFT JOIN` forces the engine to materialize all users (even those with zero orders) before the `HAVING` filter can discard them. | Switch to an `INNER JOIN`. The `HAVING order_count > 5` already guarantees that only users with at least one order survive, so an inner join is logically equivalent and cheaper. |
| **COUNT(o.id)** | Counting a nullable column forces the engine to check for nulls. | Use `COUNT(*)` – it’s faster and semantically identical in this context. |
| **GROUP BY u.id only** | In MySQL with `ONLY_FULL_GROUP_BY`, `u.name` must appear in the `GROUP BY` or be aggregated. | Either add `u.name` to the `GROUP BY` or use `SELECT u.id, u.name, ...` with `GROUP BY u.id, u.name`. PostgreSQL is fine as `id` is the primary key. |
| **SUM(o.total)** | If `orders.total` is a `DECIMAL` or `NUMERIC`, summing can be expensive on a large dataset. | The covering index `orders(user_id, total)` lets the engine read the totals directly from the index pages, avoiding a heap read. |
| **Sorting all rows** | `ORDER BY total_spent DESC` forces a full sort of the result set. | If you only need the top N users, add `LIMIT N`. The optimizer can then use a *top‑N* sort or a partial sort. |
| **Missing statistics** | If the optimizer’s statistics are stale, it may choose a bad plan (e.g., full table scan). | Run `ANALYZE` (PostgreSQL) or `ANALYZE TABLE` (MySQL) after large data changes. |
| **Potentially large intermediate result** | The join can produce a huge intermediate table before aggregation. | The composite index on `orders(user_id, total)` allows the engine to perform an *index‑only* aggregation, drastically reducing I/O. |
### Rewritten query (PostgreSQL style)
```sql
SELECT
u.id,
u.name,
COUNT(*) AS order_count,
SUM(o.total) AS total_spent
FROM users u
JOIN orders o
ON u.id = o.user_id
WHERE u.created_at > '2024-01-01'
GROUP BY u.id, u.name
HAVING COUNT(*) > 5
ORDER BY total_spent DESC
LIMIT 100; -- optional, if you only need the top 100
```
*Why this version is better*
1. **INNER JOIN** – eliminates unnecessary rows early.
2. **COUNT(*)** – faster than `COUNT(o.id)`.
3. **GROUP BY u.id, u.name** – satisfies `ONLY_FULL_GROUP_BY` and keeps the plan simple.
4. **LIMIT** – optional but can cut the sort cost if you only need a subset.
5. **Indexes** – with `users(created_at, id)` and `orders(user_id, total)` the planner can do an *index‑only* scan and aggregation.
---
## Quick checklist for the DBA
1. **Verify indexes**
- `users(created_at, id)`
- `orders(user_id, total)`
2. **Run `EXPLAIN`** on the current query and on the rewritten version.
- Look for *Index Scan* vs *Seq Scan*.
- Check that the aggregation is done on the index pages.
3. **Check statistics** – run `ANALYZE` if needed.
4. **Test with realistic data volume** – confirm that the plan changes as expected.
5. **Monitor** – after deployment, watch the query’s runtime and I/O to ensure the changes had the intended effect.
With these changes you should see a noticeable drop in CPU, I/O, and overall latency for this aggregation.[0m
================================================================================
=== COMPLEX REASONING DEMO ===
--- Query Debugging Example ---
[94mLet's go through each step to debug the slow SQL query.
**Step 1: Analyze the execution plan**
The execution statistics provide some information about the query's performance, but an actual execution plan would be more detailed. However, based on the provided statistics, we can make some inferences.
* The query takes 15.2 seconds to execute, which is slow.
* 50 million rows are examined, but only 25,000 rows are returned. This suggests that the query is doing a lot of unnecessary work.
* Two temporary tables are created, which can be a sign of inefficient joins or sorting.
* The presence of a filesort operation indicates that the database is sorting data on disk, which can be slow.
The bottlenecks appear to be:
* The large number of rows examined, indicating inefficient filtering or joining.
* The use of temporary tables and filesort, which can be slow.
**Step 2: Identify performance issues**
Based on the query and execution statistics, the following performance issues can be identified:
* **Inefficient joins**: The query uses old-style joins (comma-separated tables in the FROM clause) instead of explicit JOIN syntax. This can lead to slower performance and more temporary tables.
* **Missing indexes**: There are no indexes mentioned in the query or execution statistics. It's likely that indexes are missing on the join columns (o.user_id, o.product_id, u.id, and p.id).
* **Inefficient filtering**: The query is examining 50 million rows but only returning 25,000 rows. This suggests that the filtering conditions are not efficient.
**Step 3: Propose solutions**
To address the performance issues, the following solutions can be proposed:
* **Rewrite the query using explicit JOIN syntax**: Replace the comma-separated tables with explicit JOINs to improve readability and performance.
* **Add indexes on join columns**: Create indexes on o.user_id, o.product_id, u.id, and p.id to speed up the joins.
* **Optimize filtering conditions**: Consider adding additional filtering conditions or reordering the joins to reduce the number of rows examined.
Example rewritten query:
```sql
SELECT *
FROM orders o
JOIN users u ON o.user_id = u.id
JOIN products p ON o.product_id = p.id;
```
**Step 4: Estimate impact**
The impact of these changes can be estimated as follows:
* **Indexing join columns**: This can reduce the number of rows examined and speed up the joins. Estimated improvement: 30-50% reduction in execution time.
* **Rewriting the query**: This can improve readability and performance. Estimated improvement: 10-20% reduction in execution time.
* **Optimizing filtering conditions**: This can reduce the number of rows examined and speed up the query. Estimated improvement: 20-30% reduction in execution time.
Overall, the estimated improvement in execution time is 50-80%. However, the actual improvement may vary depending on the specific database schema, data distribution, and system configuration.
Trade-offs:
* Adding indexes can increase storage space and slow down write operations.
* Rewriting the query may require additional testing and validation.
* Optimizing filtering conditions may require additional analysis and experimentation.[0m
============================================================
--- Schema Design Example ---
[94mI'll guide you through the systematic design of a database schema for the e-commerce platform.
**Step 1: Identify Entities**
Let's identify the main objects/concepts and their key attributes:
1. **Users**
* User ID (unique identifier)
* Name
* Email
* Password (hashed)
* Shipping addresses (multiple)
* Payment methods (multiple)
2. **Products**
* Product ID (unique identifier)
* Name
* Description
* Price
* Category (foreign key referencing Categories)
* Variants (multiple, e.g., size, color)
3. **Categories**
* Category ID (unique identifier)
* Name
* Description
4. **Orders**
* Order ID (unique identifier)
* User ID (foreign key referencing Users)
* Order date
* Total cost
* Status (e.g., pending, shipped, delivered)
5. **Order Items**
* Order Item ID (unique identifier)
* Order ID (foreign key referencing Orders)
* Product ID (foreign key referencing Products)
* Quantity
* Price (at the time of order)
6. **Product Variants**
* Variant ID (unique identifier)
* Product ID (foreign key referencing Products)
* Attribute (e.g., size, color)
* Value (e.g., "Large", "Red")
* Inventory level
7. **Shipping Addresses**
* Address ID (unique identifier)
* User ID (foreign key referencing Users)
* Street
* City
* State
* ZIP
* Country
8. **Payment Methods**
* Payment Method ID (unique identifier)
* User ID (foreign key referencing Users)
* Type (e.g., credit card, PayPal)
* Details (e.g., card number, expiration date)
9. **Discount Codes**
* Discount Code ID (unique identifier)
* Code
* Discount percentage
* Expiration date
10. **Returns**
* Return ID (unique identifier)
* Order ID (foreign key referencing Orders)
* Product ID (foreign key referencing Products)
* Quantity
* Reason
11. **Refunds**
* Refund ID (unique identifier)
* Return ID (foreign key referencing Returns)
* Amount
* Date
12. **Analytics**
* Event ID (unique identifier)
* User ID (foreign key referencing Users)
* Event type (e.g., page view, purchase)
* Timestamp
**Step 2: Define Relationships**
Now, let's define the relationships between entities:
1. A user can have multiple shipping addresses (1:N).
2. A user can have multiple payment methods (1:N).
3. A product belongs to one category (1:1).
4. A product can have multiple variants (1:N).
5. An order is placed by one user (1:1).
6. An order can contain multiple order items (1:N).
7. An order item is part of one order (1:1).
8. An order item is for one product (1:1).
9. A product variant is part of one product (1:1).
10. A shipping address is associated with one user (1:1).
11. A payment method is associated with one user (1:1).
12. A discount code can be applied to multiple orders (N:N).
13. A return is for one order (1:1).
14. A refund is for one return (1:1).
15. An analytics event is associated with one user (1:1).
**Step 3: Normalize the Design**
To normalize the design, we'll aim for 3NF (Third Normal Form). We'll eliminate redundant data and ensure that each table has a primary key.
1. Split the **Products** table into **Products** and **Product Variants** to eliminate redundant data.
2. Create a separate **Discount Codes** table to store discount codes and their details.
3. Create a separate **Returns** table to store return information.
4. Create a separate **Refunds** table to store refund information.
5. Create a separate **Analytics** table to store analytics events.
**Step 4: Consider Performance**
To improve performance, we'll consider the following:
1. Add indexes on frequently queried columns, such as **Users**.**email**, **Products**.**name**, and **Orders**.**order_date**.
2. Denormalize the **Order Items** table by storing the product name and price at the time of order to reduce joins.
3. Consider using a materialized view for analytics data to improve query performance.
**Step 5: Plan for Scale**
To plan for scale, we'll consider the following:
1. Use a distributed database or a cloud-based database service to handle increased traffic and data volume.
2. Implement sharding or partitioning to distribute data across multiple servers.
3. Use caching mechanisms, such as Redis or Memcached, to reduce database queries.
4. Monitor database performance and adjust indexing, caching, and sharding strategies as needed.
**Final Schema**
Here is the final database schema:
```sql
CREATE TABLE Users (
user_id INT PRIMARY KEY,
name VARCHAR(255),
email VARCHAR(255) UNIQUE,
password VARCHAR(255)
);
CREATE TABLE ShippingAddresses (
address_id INT PRIMARY KEY,
user_id INT,
street VARCHAR(255),
city VARCHAR(255),
state VARCHAR(255),
zip VARCHAR(255),
country VARCHAR(255),
FOREIGN KEY (user_id) REFERENCES Users(user_id)
);
CREATE TABLE PaymentMethods (
payment_method_id INT PRIMARY KEY,
user_id INT,
type VARCHAR(255),
details VARCHAR(255),
FOREIGN KEY (user_id) REFERENCES Users(user_id)
);
CREATE TABLE Categories (
category_id INT PRIMARY KEY,
name VARCHAR(255),
description VARCHAR(255)
);
CREATE TABLE Products (
product_id INT PRIMARY KEY,
name VARCHAR(255),
description VARCHAR(255),
price DECIMAL(10, 2),
category_id INT,
FOREIGN KEY (category_id) REFERENCES Categories(category_id)
);
CREATE TABLE ProductVariants (
variant_id INT PRIMARY KEY,
product_id INT,
attribute VARCHAR(255),
value VARCHAR(255),
inventory_level INT,
FOREIGN KEY (product_id) REFERENCES Products(product_id)
);
CREATE TABLE Orders (
order_id INT PRIMARY KEY,
user_id INT,
order_date DATE,
total_cost DECIMAL(10, 2),
status VARCHAR(255),
FOREIGN KEY (user_id) REFERENCES Users(user_id)
);
CREATE TABLE OrderItems (
order_item_id INT PRIMARY KEY,
order_id INT,
product_id INT,
quantity INT,
price DECIMAL(10, 2),
FOREIGN KEY (order_id) REFERENCES Orders(order_id),
FOREIGN KEY (product_id) REFERENCES Products(product_id)
);
CREATE TABLE DiscountCodes (
discount_code_id INT PRIMARY KEY,
code VARCHAR(255),
discount_percentage DECIMAL(5, 2),
expiration_date DATE
);
CREATE TABLE Returns (
return_id INT PRIMARY KEY,
order_id INT,
product_id INT,
quantity INT,
reason VARCHAR(255),
FOREIGN KEY (order_id) REFERENCES Orders(order_id),
FOREIGN KEY (product_id) REFERENCES Products(product_id)
);
CREATE TABLE Refunds (
refund_id INT PRIMARY KEY,
return_id INT,
amount DECIMAL(10, 2),
date DATE,
FOREIGN KEY (return_id) REFERENCES Returns(return_id)
);
CREATE TABLE Analytics (
event_id INT PRIMARY KEY,
user_id INT,
event_type VARCHAR(255),
timestamp TIMESTAMP,
FOREIGN KEY (user_id) REFERENCES Users(user_id)
);
```
This schema should support the e-commerce platform's requirements while ensuring data consistency, scalability, and performance.[0m
For a comprehensive collection of prompting techniques and examples, check out the Prompt Engineering Guide. It's an excellent resource that covers everything from basic prompts to advanced techniques like tree-of-thought reasoning.
3. Advanced Prompting Patterns
Now for the tricks that separate amateur hour from production-ready systems.
Role-Playing Prompts: More Than Just "You Are A..."
The difference between "You are a SQL expert" and a proper role definition? About 10x in output quality.
def create_expert_analyzer(expertise_level: str = "senior"):
"""Create specialized SQL analyzer with detailed role definition"""
roles = {
"junior": "You are a junior developer learning SQL best practices.",
"senior": ("You are a senior database architect with 15 years "
"optimizing Fortune 500 databases."),
"security": ("You are a database security specialist focused on "
"SQL injection prevention.")
}
def analyze(query: str, context: str = "") -> str:
system_prompt = f"""
{roles.get(expertise_level, roles['senior'])}
Your approach:
- Identify issues before suggesting fixes
- Explain trade-offs, not just solutions
- Consider the business context
- Provide actionable recommendations
Response format:
1. ISSUES FOUND: [list]
2. IMPACT: [business impact]
3. RECOMMENDATIONS: [specific fixes]
4. ALTERNATIVE APPROACHES: [if applicable]
"""
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{"role": "system", "content": system_prompt},
{"role": "user", "content": f"Context: {context}\n\nQuery: {query}"}
],
temperature=0.3
)
return response["choices"][0]["message"]["content"]
return analyze
# Usage
security_analyzer = create_expert_analyzer("security")
result = security_analyzer(
"SELECT * FROM users WHERE username = '" + user_input + "'",
context="Public-facing login system"
)
# Returns detailed security analysis with SQL injection warnings
Run this example yourself 🔧
Script:
4_role_playing_prompts.py
Command:
uv run 4_role_playing_prompts.pyExpected Output:
Role-Playing Prompts Demo
=== ROLE-BASED ANALYSIS COMPARISON ===
Query: SELECT * FROM users WHERE username = 'user_input'
Context: Public-facing login system with 10M users
============================================================
--- JUNIOR PERSPECTIVE ---
[94m**1. ISSUES FOUND**
- **SELECT ***: pulls all columns, even those not needed, increasing I/O and memory usage.
- **No column list**: makes the query harder to maintain and can expose sensitive data (e.g., password hashes).
- **Missing index on `username`**: a full table scan on a 10M‑row table will be slow.
- **No parameterization**: the literal `'user_input'` suggests the query may be built by string concatenation, opening the door to SQL injection.
- **No `LIMIT 1`**: if usernames are unique, the query still scans the entire index/cluster to find all matches.
- **No password verification**: the query only fetches the row; the application must still handle authentication logic, which can be error‑prone if not done securely.
- **Potential for duplicate usernames**: if the schema allows duplicates, the query may return multiple rows, complicating login logic.
**2. IMPACT**
- **Performance**: Full scans on a 10M table can cause high CPU, memory, and disk I/O, leading to slow login responses and increased load on the database server.
- **Security**: Unparameterized queries expose the system to SQL injection attacks, potentially allowing attackers to bypass authentication or exfiltrate data.
- **Data Leakage**: Selecting all columns may inadvertently expose sensitive fields (e.g., `password_hash`, `security_question`).
- **Scalability**: As the user base grows, the lack of proper indexing and query tuning will degrade login performance, affecting user experience and potentially causing timeouts.
**3. RECOMMENDATIONS**
1. **Use a parameterized query** (prepared statement) to prevent injection.
```sql
SELECT user_id, username, password_hash, email
FROM users
WHERE username = :username
LIMIT 1;
```
2. **Specify only the columns needed** for authentication (e.g., `user_id`, `password_hash`).
3. **Add an index** on the `username` column (unique if usernames are unique).
```sql
CREATE UNIQUE INDEX idx_users_username ON users(username);
```
4. **Enforce uniqueness** at the database level if not already done.
5. **Handle password verification** in the application using a secure hashing algorithm (e.g., bcrypt, Argon2).
6. **Consider adding a `status` column** (active/inactive) and filter on it to prevent login for deactivated accounts.
7. **Use connection pooling** to reduce connection overhead for frequent login attempts.
**4. ALTERNATIVE APPROACHES**
- **Stored Procedure**: Encapsulate the lookup and password hash retrieval in a stored procedure, returning only a success flag or user ID.
- **ORM or Query Builder**: Use a framework that automatically parameterizes queries and maps results to objects, reducing boilerplate and risk.
- **Caching**: For high‑traffic systems, cache the result of successful logins (e.g., in Redis) to avoid hitting the database on every attempt, while still validating the password hash on the first request.
Implementing these changes will improve performance, enhance security, and make the login flow more maintainable as the user base grows.[0m
----------------------------------------
--- SENIOR PERSPECTIVE ---
[94m**1. ISSUES FOUND**
| # | Issue | Why it matters |
|---|-------|----------------|
| 1 | **SELECT *** – pulling every column for every lookup | Increases I/O, memory usage, and network traffic. With 10 M users, a single login request can read dozens of KBs. |
| 2 | **Missing index on `username`** | A full table scan on a 10 M row table is O(n). Even with a B‑tree index, a missing one forces a scan, causing high CPU and I/O. |
| 3 | **Potential SQL injection** | The query string is built from user input (`'user_input'`) without parameterization. |
| 4 | **No uniqueness enforcement** | If `username` is not unique, the query may return multiple rows, leading to ambiguous logins. |
| 5 | **No caching / read‑replica strategy** | Every login hits the primary, creating a bottleneck under peak traffic. |
| 6 | **No consideration of data type / length** | If `username` is stored as a variable‑length type (e.g., VARCHAR(255)), the index can be large and slow. |
| 7 | **No connection pooling** | Re‑establishing connections for each login adds latency and resource consumption. |
| 8 | **No monitoring / alerting** | Without metrics, you can’t detect slow queries or index fragmentation. |
---
**2. IMPACT**
| Impact | Business Effect |
|--------|-----------------|
| **Performance degradation** | Users experience slow logins, higher latency, and possible timeouts during peak hours. |
| **Scalability limits** | The system cannot easily handle traffic spikes (e.g., marketing campaigns, product launches). |
| **Security risk** | SQL injection could allow attackers to bypass authentication or exfiltrate data. |
| **Operational cost** | Higher CPU, I/O, and network usage increase hosting costs and may require larger hardware. |
| **User churn** | Poor login experience can lead to lost customers and negative brand perception. |
---
**3. RECOMMENDATIONS**
| # | Fix | Implementation Steps | Trade‑offs |
|---|-----|----------------------|------------|
| 1 | **Parameterize the query** | Use prepared statements (e.g., `SELECT * FROM users WHERE username = ?`). | None; improves security and allows plan caching. |
| 2 | **Index `username`** | `CREATE UNIQUE INDEX idx_users_username ON users(username);` | Index maintenance cost on writes; ensure `username` is unique. |
| 3 | **Select only needed columns** | `SELECT user_id, password_hash, last_login FROM users WHERE username = ?;` | Reduces I/O; if you need more columns later, adjust accordingly. |
| 4 | **Enforce uniqueness** | Add `UNIQUE` constraint on `username` if not already present. | Prevents duplicate accounts; may require data cleanup. |
| 5 | **Use connection pooling** | Configure your application server (e.g., HikariCP, PgBouncer) to reuse connections. | Slightly more memory usage; reduces connection overhead. |
| 6 | **Implement read replicas** | Route login queries to a read‑only replica; write traffic stays on primary. | Requires eventual consistency; additional infrastructure cost. |
| 7 | **Cache frequent lookups** | Cache username → user_id mapping in Redis or Memcached for a short TTL (e.g., 5 min). | Cache invalidation complexity; stale data risk if user updates password. |
| 8 | **Optimize data type** | Store `username` as `VARCHAR(64)` or `CHAR(32)` if length is bounded. | Smaller index size; restricts maximum username length. |
| 9 | **Monitor query performance** | Enable slow‑query logs, use APM tools, set alerts on query latency > 10 ms. | Requires monitoring setup; adds overhead if logs are too verbose. |
|10 | **Consider partitioning** | Range or hash partition on `user_id` or `created_at` if you anticipate table growth beyond 10 M. | Adds complexity; may not be needed until > 50 M rows. |
**Action Plan (first 30 days)**
1. **Audit**: Verify `username` uniqueness; run `SELECT username, COUNT(*) FROM users GROUP BY username HAVING COUNT(*) > 1;`
2. **Index**: Create the unique index; monitor write latency impact.
3. **Refactor**: Update all login code to use prepared statements and selective columns.
4. **Deploy**: Add a lightweight caching layer for username lookups.
5. **Monitor**: Set up slow‑query alerts; track login latency before/after changes.
6. **Review**: After 30 days, evaluate cost vs. performance gains; decide on replicas or partitioning.
---
**4. ALTERNATIVE APPROACHES**
| Approach | When to Use | Pros | Cons |
|----------|-------------|------|------|
| **Full‑text search on `username`** | If you need fuzzy matching or autocomplete. | Handles typos, partial matches. | Index heavier; slower exact lookups; more complex queries. |
| **Hash‑based lookup** | If usernames are highly variable and you want fixed‑size keys. | Fixed index size; faster equality checks. | Requires storing hash; risk of collisions (though negligible with 64‑bit). |
| **NoSQL (e.g., DynamoDB)** | If you anticipate massive horizontal scaling and key‑value access patterns. | Auto‑scaling, high availability. | Loss of relational features; different consistency model. |
| **Serverless functions with in‑memory DB** | For low‑traffic, cost‑optimized environments. | Zero‑maintenance, pay‑per‑use. | Not suitable for 10 M users; cold‑start latency. |
---
**Bottom line:**
Start with the simplest, most impactful changes: parameterize the query, index `username`, and only needed columns. These steps provide immediate performance and security benefits with minimal operational overhead. From there, layer caching, connection pooling, and read replicas to meet the scalability demands of a public‑facing login system with millions of users.[0m
----------------------------------------
--- SECURITY PERSPECTIVE ---
[94m**1. ISSUES FOUND**
| # | Issue | Why it matters |
|---|-------|----------------|
| 1 | **SQL Injection** – The query concatenates user input directly into the SQL string. | An attacker can inject arbitrary SQL (e.g., `username = 'admin' OR 1=1 --`) to bypass authentication or dump data. |
| 2 | **Retrieving All Columns (`SELECT *`)** – The query returns every column in the `users` table. | Sensitive data (password hashes, email, SSN, etc.) may be exposed unnecessarily, increasing the attack surface. |
| 3 | **No Password Hashing / Verification** – The query only checks the username; no password comparison is shown. | If passwords are stored in plain text or weakly hashed, a breach exposes all credentials. |
| 4 | **No Input Validation / Sanitization** – The raw `user_input` is used without checks. | Allows injection, enumeration, and other malicious payloads. |
| 5 | **No Rate‑Limiting / Brute‑Force Protection** – The snippet shows no throttling. | Facilitates credential stuffing or brute‑force attacks. |
| 6 | **Potential for Enumeration** – Query returns a row if the username exists. | An attacker can confirm valid usernames by timing or response differences. |
| 7 | **Lack of Least‑Privilege Database Access** – The query likely runs under a privileged DB user. | If compromised, the attacker can perform destructive operations. |
| 8 | **No Logging / Auditing** – No mention of logging failed login attempts. | Hard to detect or investigate attacks. |
---
**2. IMPACT**
- **Data Breach**: Successful injection can expose all user records, including password hashes and personal data.
- **Account Takeover**: Attackers can log in as any user, leading to fraud, phishing, or further lateral movement.
- **Reputational Damage**: Public-facing services with 10 M users are high‑profile targets; a breach erodes trust and can trigger regulatory penalties.
- **Financial Loss**: Costs from remediation, legal fees, and potential fines (e.g., GDPR, CCPA).
- **Operational Downtime**: Mitigation may require service interruption, affecting user experience.
---
**3. RECOMMENDATIONS**
| # | Fix | Trade‑offs | Implementation |
|---|-----|------------|----------------|
| 1 | **Use Parameterized Queries / Prepared Statements** | Slight overhead of preparing statements, but negligible for login flows. | In PHP: `$stmt = $pdo->prepare('SELECT id, username, password_hash FROM users WHERE username = :u'); $stmt->execute([':u' => $username]);` |
| 2 | **Select Only Needed Columns** | Reduces data transfer and exposure. | `SELECT id, username, password_hash FROM users WHERE username = :u` |
| 3 | **Hash Passwords with Argon2id / bcrypt** | Requires storage of salt & cost factor; slower verification but secure. | Use `password_hash()` / `password_verify()` in PHP. |
| 4 | **Validate & Sanitize Input** | Adds a small validation layer; improves UX. | Enforce username regex (`^[a-zA-Z0-9_]{3,30}$`). |
| 5 | **Implement Rate‑Limiting & Account Lockout** | May inconvenience legitimate users; balance thresholds. | Use Redis or in‑memory counters; lock after 5 failed attempts per 15 min. |
| 6 | **Use Least‑Privilege DB User** | Requires database re‑configuration; may need application refactor. | Create `app_user` with only SELECT on `users`. |
| 7 | **Log All Authentication Attempts** | Generates log volume; ensure log rotation. | Log to a dedicated audit table or external SIEM. |
| 8 | **Add Multi‑Factor Authentication (MFA)** | Extra step for users; improves security. | Integrate TOTP or WebAuthn. |
| 9 | **Implement Account Enumeration Mitigation** | Slight performance cost for timing attacks. | Return generic “Invalid credentials” message; use constant‑time comparison. |
|10 | **Use a Web Application Firewall (WAF)** | Adds cost and complexity; can block obvious injection patterns. | Deploy ModSecurity or cloud WAF. |
---
**4. ALTERNATIVE APPROACHES**
| # | Approach | When to Consider | Pros | Cons |
|---|----------|------------------|------|------|
| 1 | **ORM / Query Builder** | If you’re already using an ORM (e.g., Doctrine, Sequelize). | Automatic parameterization, abstraction. | Learning curve; potential for mis‑use if raw queries are still allowed. |
| 2 | **Identity‑as‑a‑Service (OAuth2 / OpenID Connect)** | If you want to outsource authentication. | Offloads security, MFA built‑in. | Requires integration with third‑party provider; user data control shifts. |
| 3 | **Server‑Side Session Tokens** | Replace plaintext password checks with token‑based auth. | Stateless, scalable. | Requires secure token issuance and storage. |
| 4 | **GraphQL with Resolvers** | If you’re building a modern API. | Fine‑grained field selection. | Complexity; still need to guard against injection in resolvers. |
---
**Action Plan (First 30 days)**
1. **Immediate**: Refactor login endpoint to use prepared statements and hash verification.
2. **Week 1–2**: Configure least‑privilege DB user; audit existing permissions.
3. **Week 2–3**: Implement rate‑limiting and generic error messages.
4. **Month 1**: Deploy WAF and enable logging/auditing.
5. **Month 2–3**: Roll out MFA for high‑risk accounts; evaluate third‑party auth options.
By addressing the injection vector first and layering additional controls, you’ll protect the 10 M‑user base while maintaining performance and user experience.[0m
----------------------------------------
--- CONSULTANT PERSPECTIVE ---
[94m**1. ISSUES FOUND**
| # | Issue | Why it matters |
|---|-------|---------------|
| 1 | **SQL Injection risk** – The query concatenates user input directly into the SQL string. | Allows attackers to execute arbitrary SQL, potentially exfiltrating or corrupting data. |
| 2 | **SELECT *** – Retrieving all columns, including sensitive fields (e.g., password_hash, SSN, audit logs). | Increases I/O, network traffic, and exposes data that should never be sent to the application layer. |
| 3 | **No index on `username`** – Assuming `username` is not indexed or is a non‑unique column. | Full table scans on a 10M‑row table cause high latency and CPU usage, degrading login performance. |
| 4 | **No uniqueness guarantee** – If `username` is not unique, the query may return multiple rows. | Ambiguous authentication, potential race conditions, and confusing user experience. |
| 5 | **No rate‑limiting / throttling** – The query can be called repeatedly, enabling brute‑force or denial‑of‑service attacks. | Increased load, potential downtime, and higher infrastructure costs. |
| 6 | **No hashing or salting shown** – The snippet does not show password verification. | If passwords are stored in plaintext or weakly hashed, the system is vulnerable to credential theft. |
| 7 | **No connection pooling** – Implicitly creating a new connection per query. | Higher connection overhead, increased latency, and resource exhaustion. |
| 8 | **No caching** – Every login hits the database. | Unnecessary load on the primary DB, higher latency, and higher operational costs. |
---
**2. IMPACT**
| Impact | Business Effect |
|-------|----------------|
| **Security breach** | Loss of customer trust, regulatory fines (GDPR, PCI‑DSS), potential legal action. |
| **Performance degradation** | Slow login times → churn, lost revenue, increased support tickets. |
| **Operational cost** | Higher CPU/memory usage, need for scaling (more servers, replicas). |
| **Compliance risk** | Failure to meet data protection regulations, leading to penalties. |
| **Reputation damage** | Negative publicity, loss of competitive edge. |
---
**3. RECOMMENDATIONS**
1. **Use Prepared Statements / Parameterized Queries**
```sql
SELECT user_id, username, password_hash, email
FROM users
WHERE username = ?
```
*Trade‑off:* Slightly more code, but eliminates injection risk.
2. **Index the `username` column** (unique if business logic requires).
```sql
CREATE UNIQUE INDEX idx_users_username ON users(username);
```
*Trade‑off:* Index maintenance cost, but improves lookup speed dramatically.
3. **Select only required columns** (omit password_hash, SSN, audit fields).
*Trade‑off:* Slightly more complex SELECT, but reduces data transfer and exposure.
4. **Enforce uniqueness on `username`** via a UNIQUE constraint.
*Trade‑off:* Requires migration if duplicates exist; prevents ambiguous logins.
5. **Implement rate‑limiting / CAPTCHA** on login endpoints.
*Trade‑off:* Adds user friction but protects against brute‑force attacks.
6. **Hash passwords with Argon2id (or bcrypt/BCrypt) + per‑user salt**.
*Trade‑off:* Slightly slower hashing, but vastly improves security.
7. **Use connection pooling** (e.g., PgBouncer, HikariCP).
*Trade‑off:* Requires configuration, but reduces latency.
8. **Cache successful login sessions** in Redis or Memcached.
*Trade‑off:* Adds a caching layer, but reduces DB load.
9. **Audit and monitor** login attempts (log, alert on anomalies).
*Trade‑off:* Requires monitoring tools, but improves incident response.
10. **Consider read replicas** for login queries to offload the primary.
*Trade‑off:* Extra infrastructure cost, but improves scalability.
---
**4. ALTERNATIVE APPROACHES**
| Approach | When to Use | Pros | Cons |
|---------|------------|------|------|
| **Stored Procedure** | If you want to encapsulate logic in the DB and enforce security centrally. | Centralized logic, easier to audit. | Requires DB admin expertise; harder to version control. |
| **NoSQL (e.g., DynamoDB)** | If you need horizontal scalability and eventual consistency. | Handles massive scale, flexible schema. | Loss of ACID guarantees; more complex consistency handling. |
| **OAuth2 / OpenID Connect** | If you want to delegate authentication to a third‑party provider. | Offloads security, reduces compliance burden. | Requires integration effort; dependency on external provider. |
| **Serverless Functions** | If you want to auto‑scale login logic. | No server management, cost‑effective. | Cold‑start latency; vendor lock‑in. |
---
**Bottom line:**
Implementing parameterized queries, indexing, column‑specific selects, and proper password hashing will immediately reduce security risk and improve login performance, saving you infrastructure costs and protecting your brand reputation. The trade‑offs mainly involve minor code changes and a small increase in infrastructure complexity, but the business benefits far outweigh the costs.[0m
----------------------------------------
================================================================================
=== INDUSTRY-SPECIFIC ANALYSIS ===
Query:
SELECT user_id, COUNT(*) as transaction_count, SUM(amount) as total_amount
FROM transactions
WHERE created_at > NOW() - INTERVAL 1 DAY
GROUP BY user_id
HAVING total_amount > 10000
Context: Daily suspicious activity report
============================================================
--- FINTECH INDUSTRY ---
[94mBelow is a “check‑list” style guide that blends the technical details of the query you posted with the compliance, performance, and risk‑management imperatives that are typical of a regulated fintech environment.
Feel free to cherry‑pick the items that fit your stack (PostgreSQL, MySQL, Oracle, etc.) and the level of automation you already have in place.
---
## 1. Query‑level best practices
| Item | Why it matters | How to implement |
|------|----------------|------------------|
| **Use deterministic time functions** | `NOW()` is session‑dependent; if your DB is in UTC but your app uses local time, you can get off‑by‑one‑day errors. | Replace `NOW()` with `CURRENT_TIMESTAMP AT TIME ZONE 'UTC'` (PostgreSQL) or `UTC_TIMESTAMP()` (MySQL). |
| **Avoid `HAVING` on aliased columns** | Some engines (e.g., older MySQL) don’t allow aliases in `HAVING`. | Use `HAVING SUM(amount) > 10000` or wrap the query in a sub‑select. |
| **Explicit column list** | Prevents accidental schema drift and makes the intent crystal clear for auditors. | Keep the SELECT list minimal and document each column’s business meaning. |
| **Use `COUNT(*)` only when you need the exact count** | `COUNT(*)` scans the whole row; if you only need “> 0” you can use `EXISTS`. | For fraud alerts, you might only need to know that a user exceeded the threshold, not the exact count. |
| **Avoid `GROUP BY` on non‑indexed columns** | Can lead to full table scans. | Ensure `user_id` is indexed (ideally a composite index with `created_at`). |
---
## 2. Indexing & Partitioning
| Strategy | Benefit | Example |
|----------|---------|---------|
| **Composite index on `(created_at, user_id, amount)`** | Enables the query to by date, then group by user, and sum amounts without a full scan. | `CREATE INDEX idx_txn_date_user_amount ON transactions (created_at, user_id, amount);` |
| **Range partitioning on `created_at`** | Keeps the “last‑day” window small; partitions can be dropped nightly, reducing storage and improving query speed. | `PARTITION BY RANGE (created_at) (PARTITION p2025_08_15 VALUES LESS THAN ('2025-08-16'), …)` |
| **Clustered index on `user_id`** (if supported) | Physical ordering by user can speed up group‑by. | `CLUSTER transactions USING idx_user_id;` |
| **Covering index** | If you only need `user_id`, `created_at`, and `amount`, a covering index can satisfy the query entirely. | `CREATE INDEX idx_covering ON transactions (user_id, created_at, amount);` |
**Tip:** Run `EXPLAIN` (or the equivalent) after each change to confirm the optimizer is using the index.
---
## 3. Performance & Scaling
| Concern | Mitigation |
|---------|------------|
| **OLTP impact** | Run the report on a **read‑replica** or a **dedicated reporting cluster**. |
| **Batch window** | Schedule the job during low‑traffic hours (e.g., 02:00–04:00 UTC). |
| **Incremental aggregation** | Instead of scanning the whole table each day, maintain a **daily summary table** that you update incrementally. |
| **Materialized view** | If your DB supports it, create a materialized view that refreshes nightly. |
| **Caching** | Store the result in a fast cache (Redis, Memcached) for a short period if the same report is requested repeatedly. |
---
## 4. Compliance & Audit Trail
| Requirement | How to satisfy it |
|-------------|-------------------|
| **SOX – Accurate financial reporting** | Ensure the query runs inside a **transaction** with `READ COMMITTED` isolation (or `REPEATABLE READ` if you need a snapshot). Log the transaction ID and timestamp. |
| **PCI‑DSS – Card data protection** | Never expose raw card numbers. If `amount` is sensitive, store it encrypted at rest and decrypt only in the reporting layer. |
| **Audit trail** | Log every execution of the report: user, start/end time, rows processed, and any errors. Store logs in an immutable, tamper‑evident store (e.g., append‑only file, blockchain, or a dedicated audit DB). |
| **Data retention** | Keep the raw transaction data for the period required by regulation (e.g., 7 years for SOX). The summary table can be purged after the same period. |
| **Access control** | Grant the reporting role **only** SELECT privileges on the `transactions` table and the summary table. Use role‑based access control (RBAC) and enforce least privilege. |
| **Encryption** | Use Transparent Data Encryption (TDE) for the database and TLS for all connections. |
| **Segregation of duties** | The person who writes the query should not be the same person who reviews the results. Use separate accounts for query execution and result review. |
---
## 5. Risk Tolerance & Business Impact
| Risk | Mitigation |
|------|------------|
| **False positives** | Add additional filters (e.g., transaction type, merchant category) to reduce noise. |
| **Missing a fraud event** | Run a secondary “high‑volume” alert that triggers on any user with > 10 transactions in the last day, regardless of amount. |
| **Performance degradation** | Monitor query runtime and set alerts if it exceeds a threshold (e.g., 30 s). |
| **Data loss** | Implement automated backups and point‑in‑time recovery. Test restores quarterly. |
---
## 6. Sample Implementation (PostgreSQL)
```sql
-- 1. Create a covering index
CREATE INDEX IF NOT EXISTS idx_txn_covering
ON transactions (user_id, created_at, amount);
-- 2. (Optional) Partition the table by day
-- (requires PostgreSQL 10+ and careful maintenance)
-- 3. Create a materialized view for the daily report
CREATE MATERIALIZED VIEW IF NOT EXISTS mv_daily_suspicious
AS
SELECT user_id,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
WHERE created_at >= (CURRENT_DATE - INTERVAL '1 day')
AND created_at < CURRENT_DATE
GROUP BY user_id
HAVING SUM(amount) > 10000
WITH DATA;
-- 4. Refresh the view nightly
REFRESH MATERIALIZED VIEW CONCURRENTLY mv_daily_suspicious;
-- 5. Query the view for reporting
SELECT * FROM mv_daily_suspicious;
```
**Audit logging (example using `pg_audit`):**
```sql
-- Enable pg_audit for SELECT statements
ALTER SYSTEM SET pgaudit.log = 'read';
SELECT pg_reload_conf();
```
---
## 7. Checklist for Deployment
1. **Index & partition** – Verify `EXPLAIN` shows index usage.
2. **Test on a replica** – Run the query on a read‑only copy to gauge performance.
3. **Audit log** – Confirm that each execution is recorded in the audit table.
4. **Compliance review** – Have your compliance officer sign off on the data handling procedures.
5. **Monitoring** – Set up alerts for query runtime, error rates, and data freshness.
6. **Backup & DR** – Verify that the transaction table and the materialized view can be restored within the required RTO/RPO.
---
### Bottom line
- **Performance**: Index, partition, or materialize the aggregation.
- **Compliance**: Encrypt, audit, and enforce RBAC.
- **Reliability**: Run on a replica, log every run, and keep immutable audit trails.
- **Risk**: Add secondary alerts, monitor thresholds, and test restores.
Implementing these steps will give you a robust, compliant, and high‑performance daily suspicious‑activity report that satisfies SOX, PCI‑DSS, and your internal risk appetite.[0m
----------------------------------------
--- ECOMMERCE INDUSTRY ---
[94m## 1. Quick‑look on the current query
```sql
SELECT user_id,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
WHERE created_at > NOW() - INTERVAL 1 DAY
GROUP BY user_id
HAVING total_amount > 10000;
```
* **Goal** – Spot users who spent > $10 k in the last 24 h.
* **Data volume** – In a large e‑commerce platform this can be millions of rows per day.
* **Business criticality** – High (fraud detection, compliance, real‑time alerts).
* **Risk tolerance** – Low (missed fraud → financial loss & regulatory fines).
* **Regulatory context** – PCI‑DSS, GDPR, CCPA, etc. → need auditability, data minimisation, retention controls.
---
## 2. Performance & Scalability Recommendations
| Area | Recommendation | Why it matters |
|------|----------------|----------------|
| **Partitioning** | **Range partition on `created_at`** (daily or hourly). | Keeps the “last‑24‑h” window in a single partition; reduces scan size dramatically. |
| **Clustering / Secondary Index** | **Cluster by `user_id`** inside each partition (or create a composite covering index on `(created_at, user_id, amount)`). | Enables the engine to skip rows that don’t belong to a user, and to use the index for the `SUM`/`COUNT`. |
| **Covering Index** | `CREATE INDEX idx_txn_daily ON transactions (created_at, user_id, amount) INCLUDE (amount)` (or equivalent in your RDBMS). | The query can be satisfied entirely from the index, no heap look‑ups. |
| **Materialised View / Incremental Aggregation** | Create a daily materialised view (or a “fraud‑snapshot” table) that aggregates per‑user totals for the last 24 h, refreshed every 5 min. | Offloads the heavy aggregation from the OLTP system; the view can be queried instantly. |
| **Columnar Store / Data Warehouse** | Push the `transactions` table to a columnar warehouse (Snowflake, Redshift, BigQuery, ClickHouse). | Analytical queries (COUNT/SUM) run orders of magnitude faster on columnar formats. |
| **Caching Layer** | Cache the result of the last 24 h query in Redis or an in‑memory store. | Real‑time alerts can read from cache; only recompute on schedule or when new data arrives. |
| **Parallelism & Query Hints** | Enable parallel execution (e.g., `PARALLEL 4`) and use hints to force index usage. | Utilises multi‑core CPUs; reduces latency for high‑concurrency workloads. |
| **Data Retention & Archiving** | Archive older partitions (e.g., > 90 days) to cheaper storage (S3, Glacier). | Keeps the active table lean; reduces I/O for the fraud query. |
| **Monitoring & Alerting** | Instrument query latency, index usage, partition growth. | Detect performance regressions early; auto‑scale resources if needed. |
---
## 3. Query Rewrite (if you keep the OLTP table)
```sql
-- 1. Use a covering index
SELECT user_id,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
WHERE created_at >= CURRENT_TIMESTAMP - INTERVAL '1' DAY
GROUP BY user_id
HAVING SUM(amount) > 10000;
```
* **Why** – `HAVING SUM(amount) > 10000` forces a full scan of the group; moving the predicate to `WHERE` (if possible) can reduce rows earlier.
* **If** you can pre‑aggregate per‑user per‑hour, you can sum those aggregates instead of raw rows.
---
## 4. Architectural Patterns
| Pattern | When to use | Example |
|---------|-------------|---------|
| **OLTP + OLAP** | Separate systems: MySQL/PostgreSQL for orders, Snowflake/Redshift for analytics. | Load‑balance writes to OLTP; run fraud queries on OLAP. |
| **Data Lakehouse** | Need both schema‑on‑write and schema‑on‑read. | Delta Lake on S3 + Spark SQL for fraud detection. |
| **Event‑Driven** | Real‑time fraud alerts. | Kafka → Kinesis → Lambda → Redis cache. |
| **Micro‑services** | Isolate fraud service. | Service reads from a dedicated “fraud” DB or cache. |
---
## 5. Compliance & Risk Controls
| Requirement | Implementation |
|-------------|----------------|
| **PCI‑DSS** | Encrypt `amount` at rest; restrict access to the `transactions` table; log all reads. |
| **GDPR / CCPA** | Store only the minimal user identifiers needed for fraud detection; enable “right to be forgotten” by deleting user rows from the active table and archiving them. |
| **Audit Trail** | Keep immutable logs of any query that touches sensitive data; use database audit logs. |
| **Data Retention** | Define retention periods (e.g., 12 months for compliance, 3 months for analytics). |
| **Access Controls** | Role‑based access: only fraud analysts can query the full table; others see only the materialised view. |
---
## 6. Risk‑Tolerant Design
* **Fail‑over** – Keep a hot standby for the fraud DB; use read replicas for reporting.
* **Back‑ups** – Daily incremental + weekly full; store in separate region.
* **Testing** – Run synthetic fraud scenarios to validate the query and alerting pipeline.
* **Rate‑limiting** – Protect the fraud service from abuse; throttle queries per user/IP.
---
## 7. Suggested Implementation Roadmap
1. **Partition & Index** – Add daily range partition on `created_at`; create covering index.
2. **Materialised View** – Build a `fraud_snapshot` table refreshed every 5 min.
3. **Move to Columnar** – Export `transactions` to a warehouse; run the query there for production alerts.
4. **Cache Layer** – Populate Redis with the latest snapshot; expose a simple API for real‑time checks.
5. **Audit & Compliance** – Enable database audit logs; enforce encryption & RBAC.
6. **Monitoring** – Set up Grafana dashboards for query latency, partition size, cache hit ratio.
7. **Iterate** – Use A/B testing to tune refresh intervals, partition granularity, and alert thresholds.
---
### Bottom line
- **Partition + cluster** → drastically cuts scan size.
- **Covering index** → eliminates heap look‑ups.
- **Materialised view / columnar warehouse** → turns a heavy OLTP aggregation into a lightning‑fast read.
- **Compliance controls** → keep the system auditable and secure.
Implementing these steps will give you a fraud‑detection pipeline that is **fast, reliable, and compliant**—exactly what you need during peak shopping periods.[0m
----------------------------------------
--- GAMING INDUSTRY ---
[94m## 1. Quick‑look on the current query
```sql
SELECT user_id,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
WHERE created_at > NOW() - INTERVAL 1 DAY
GROUP BY user_id
HAVING total_amount > 10000;
```
* **Goal** – Spot users who spent more than $10 k in the last 24 h.
* **Typical data volume** – Millions of rows per day, thousands of users per minute.
* **Latency requirement** – < 1 s for the alerting pipeline (real‑time fraud/cheat detection).
* **Business criticality** – High (prevent revenue loss, maintain player trust).
* **Risk tolerance** – Low false‑positive rate, but we can tolerate a few missed alerts if the system is under‑loaded.
---
## 2. Performance & Scalability
| Area | Recommendation | Why it matters |
|------|----------------|----------------|
| **Partitioning** | Range‑partition `transactions` on `created_at` (daily or hourly). | Keeps the 24‑h window small, reduces scan size, improves purge/archival. |
| **Indexing** | 1️⃣ Composite index on `(created_at, user_id, amount)` <br>2️⃣ Partial index: `WHERE created_at > NOW() - INTERVAL 1 DAY` (if supported). | Enables fast range scans, grouping, and aggregation. |
| **Materialized View / Aggregation Table** | Create a `daily_user_spend` table that is refreshed every minute (or via CDC). <br>Schema: `(user_id, day, transaction_count, total_amount)`. | Offloads heavy aggregation from the OLTP engine; query becomes a simple lookup. |
| **Read Replicas** | Route the suspicious‑activity query to a read‑only replica. | Keeps the primary OLTP workload unaffected. |
| **Sharding** | Horizontal shard on `user_id` (e.g., modulo 256). | Distributes load, keeps per‑node data manageable. |
| **In‑memory / Cache** | Cache the last‑24‑h aggregation in Redis or Memcached. | Zero‑latency look‑ups for real‑time alerts. |
| **Batch vs. Streaming** | Use a streaming engine (Kafka → Flink/Beam) to maintain a running total per user. | Real‑time detection without hitting the database. |
| **Query Rewrite** | Use a CTE or sub‑query to pre‑filter the 24‑h window, then aggregate: <br>```sql\nWITH recent AS (\n SELECT user_id, amount\n FROM transactions\n WHERE created_at > NOW() - INTERVAL 1 DAY\n)\nSELECT user_id, COUNT(*) AS transaction_count, SUM(amount) AS total_amount\nFROM recent\nGROUP BY user_id\nHAVING SUM(amount) > 10000;\n``` | Reduces the amount of data the engine has to process. |
---
## 3. Anti‑Cheat & Analytics Layer
| Feature | Implementation | Benefit |
|---------|----------------|---------|
| **Anomaly Detection** | Train a lightweight model (e.g., Isolation Forest) on historical spend patterns. | Flags users whose 24‑h spend deviates > 3 σ from their norm. |
| **Dynamic Threshold** | Instead of a fixed $10 k, compute a per‑user threshold: `max(10k, 5×std_dev_of_last_30_days)`. | Reduces false positives for high‑spending VIPs. |
| **Behavioral Flags** | Combine spend with other signals: rapid transaction bursts, IP geolocation changes, device fingerprint anomalies. | Multi‑factor risk scoring. |
| **Real‑time Alerting** | Push flagged users to a Kafka topic → alerting service → email/SMS/Discord webhook. | Immediate response to potential fraud. |
| **Post‑hoc Analytics** | Store flagged events in a data lake (S3/ADLS) for deeper investigation. | Enables root‑cause analysis and model retraining. |
---
## 4. Regulatory & Compliance
| Requirement | How to satisfy |
|-------------|----------------|
| **GDPR / CCPA** | Store only the minimal PII needed (user_id, IP, device_id). Encrypt at rest. Provide right‑to‑be‑forgotten via a purge job that deletes all rows for a user. |
| **PCI‑DSS** | If `amount` represents real money, ensure the `transactions` table is on a PCI‑compliant database. Use tokenization for card numbers. |
| **Audit Trail** | Every read of `transactions` that contributes to an alert must be logged (timestamp, query hash, user_id). Store logs in an immutable append‑only store (e.g., WORM S3). |
| **Data Residency** | If players are in EU, keep the data in an EU‑region. Use geo‑aware sharding. |
| **Retention Policy** | Keep raw transaction data for 12 months, aggregated view for 3 months. Archive older data to cold storage. |
---
## 5. High Availability & Disaster Recovery
| Strategy | Details |
|----------|---------|
| **Multi‑Region Replication** | Deploy the database cluster in two regions with synchronous replication for the OLTP tier. |
| **Failover Automation** | Use tools like Patroni/Citus or native cloud services (Aurora Global, Spanner) for automatic failover. |
| **Backup & Restore** | Daily full backups + incremental WAL/transaction log backups. Test restores quarterly. |
| **Chaos Engineering** | Periodically inject latency or node failures to validate alerting and failover. |
| **Circuit Breaker** | If the alerting pipeline is down, fall back to a “batch‑mode” that processes the last 24 h at the next maintenance window. |
---
## 6. Risk Management & Tuning
| Risk | Mitigation |
|------|------------|
| **False Positives** | Use dynamic thresholds, multi‑signal scoring, and manual review queue. |
| **Missed Alerts** | Keep the aggregation window slightly larger (e.g., 25 h) and use a sliding window. |
| **Data Skew** | Monitor shard sizes; rebalance if a few users dominate spend. |
| **Latency Spikes** | Cache the aggregation; if cache misses, fall back to the materialized view. |
| **Compliance Breach** | Regular penetration tests; enforce least‑privilege on DB roles. |
---
## 7. Implementation Roadmap (High‑Level)
| Phase | Tasks |
|-------|-------|
| **0 – Baseline** | Capture current query performance metrics (QPS, latency, CPU, I/O). |
| **1 – Partition & Index** | Add daily partitions; create composite index; test query on a replica. |
| **2 – Aggregation Layer** | Build `daily_user_spend` table (batch or streaming). |
| **3 – Alerting Pipeline** | Hook up Kafka → Flink/Beam → alert service. |
| **4 – Compliance Hardening** | Enable encryption, audit logs, data residency controls. |
| **5 – HA & DR** | Spin up read replicas, set up failover, run chaos tests. |
| **6 – Monitoring & Ops** | Dashboards (Prometheus + Grafana), alert thresholds, SLA tracking. |
| **7 – Continuous Improvement** | Model retraining, threshold tuning, periodic performance reviews. |
---
## 8. Quick‑Start SQL Snippet (PostgreSQL‑style)
```sql
-- 1️⃣ Partitioned table (daily)
CREATE TABLE transactions (
id BIGSERIAL PRIMARY KEY,
user_id BIGINT NOT NULL,
amount NUMERIC(12,2) NOT NULL,
created_at TIMESTAMPTZ NOT NULL,
-- other columns...
) PARTITION BY RANGE (created_at);
-- Example partition for today
CREATE TABLE transactions_2025_08_15 PARTITION OF transactions
FOR VALUES FROM ('2025-08-15 00:00:00+00') TO ('2025-08-16 00:00:00+00');
-- 2️⃣ Composite index
CREATE INDEX idx_txn_user_created_amount
ON transactions (created_at, user_id, amount);
-- 3️⃣ Materialized view for daily spend
CREATE MATERIALIZED VIEW daily_user_spend AS
SELECT user_id,
DATE_TRUNC('day', created_at) AS day,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
GROUP BY user_id, day;
-- 4️⃣ Query against the view
SELECT user_id, transaction_count, total_amount
FROM daily_user_spend
WHERE day = CURRENT_DATE
AND total_amount > 10000;
```
> **Tip:** If you’re on a cloud provider, consider using a managed analytics service (e.g., Snowflake, BigQuery) for the materialized view and let the OLTP tier stay in a low‑latency database.
---
### Bottom line
- **Partition + index** → immediate speed‑up for the 24‑h window.
- **Materialized view / streaming** → offload heavy aggregation, keep latency < 1 s.
- **Read replicas + caching** → protect the OLTP engine.
- **Dynamic, multi‑signal risk scoring** → reduce false positives while staying compliant.
- **High‑availability & audit** → meet regulatory demands and keep players trusting the platform.
Implement these layers incrementally, monitor the impact, and iterate on thresholds and models. Happy coding—and may your players stay honest![0m
----------------------------------------
--- HEALTHCARE INDUSTRY ---
[94mBelow is a quick‑fire “check‑list” that blends the **technical** side of the query you posted with the **regulatory** and **operational** realities of a healthcare data environment.
Feel free to cherry‑pick the items that apply to your stack; the goal is to keep the system **HIPAA‑compliant, auditable, and performant** while still surfacing the suspicious activity you’re after.
---
## 1. Query‑level considerations
| Item | Why it matters | Practical tip |
|------|----------------|---------------|
| **Use a read‑replica / off‑peak instance** | Avoids locking the production DB during a potentially heavy aggregation. | Schedule the job on a read‑only replica or a dedicated analytics cluster. |
| **Add an index on `(created_at, user_id, amount)`** | The `WHERE` clause filters on `created_at`, and the `GROUP BY` uses `user_id`. A composite index will let the engine scan only the last‑day slice and aggregate in‑memory. | `CREATE INDEX idx_txn_lastday ON transactions (created_at, user_id, amount);` |
| **Avoid `NOW()` in production if you need deterministic results** | `NOW()` is non‑deterministic; if the job runs across a midnight boundary you could double‑count. | Use a scheduled timestamp (`CURRENT_TIMESTAMP` at job start) or pass a fixed `:run_at` parameter. |
| **Use `HAVING SUM(amount) > 10000` instead of `total_amount`** | Some engines don’t allow alias use in `HAVING`. | `HAVING SUM(amount) > 10000` |
| **Consider a materialized view or incremental aggregation** | If the transaction table is huge, a nightly materialized view that pre‑aggregates per‑user totals can cut runtime dramatically. | `CREATE MATERIALIZED VIEW mv_daily_totals AS SELECT user_id, SUM(amount) AS total_amount FROM transactions WHERE created_at > CURRENT_DATE GROUP BY user_id;` |
| **Audit the query execution plan** | Guarantees you’re not hitting a full table scan. | `EXPLAIN ANALYZE` on the query; look for “Index Scan” on `created_at`. |
---
## 2. HIPAA & Data‑Protection
| Item | Why it matters | Practical tip |
|------|----------------|---------------|
| **Limit PHI exposure** | The query only returns `user_id`, `transaction_count`, and `total_amount`. If `user_id` is a PHI field (e.g., patient ID), you must treat the result set as PHI. | Store the output in a secure, access‑controlled table or file; encrypt at rest. |
| **Encrypt data in transit** | Even internal traffic can be intercepted. | Use TLS for all DB connections. |
| **Encrypt data at rest** | HIPAA requires encryption of PHI on disk. | Enable Transparent Data Encryption (TDE) or use file‑system encryption. |
| **Row‑level security (RLS)** | Prevents accidental exposure of PHI to users who shouldn’t see it. | Apply RLS policies that only allow the audit/monitoring role to read the result set. |
| **Audit trail** | Every query that touches PHI must be logged. | Enable database audit logs (e.g., PostgreSQL `pg_audit`, Oracle `AUDIT`, SQL Server `CIS`) and store them in a tamper‑evident repository. |
| **Data retention & deletion** | HIPAA requires you to keep logs for 6 years (or longer if state law says). | Automate archival of audit logs and purge older than the retention window. |
---
## 3. Operational & Business‑Criticality
| Item | Why it matters | Practical tip |
|------|----------------|---------------|
| **High availability (HA)** | Lives depend on the system; downtime can delay fraud detection. | Deploy the DB in a multi‑AZ cluster with automatic failover. |
| **Backup & DR** | In case of catastrophic failure, you need a recent snapshot. | Daily full backups + incremental logs; test restores quarterly. |
| **Monitoring & alerting** | Suspicious activity should trigger an alert. | Hook the query into your SIEM (Splunk, ELK, etc.) and set thresholds (e.g., >$10k in 24 h). |
| **Performance SLA** | The job must finish before the next day’s batch starts. | Benchmark the query on a replica; if > 30 s, consider partitioning the `transactions` table by date. |
| **Security hardening** | Attackers may try to inject malicious SQL. | Use parameterized queries; never concatenate user input. |
| **Compliance reporting** | Some regulators require you to report suspicious activity. | Export the result set to a secure CSV/JSON and feed it into the compliance portal. |
---
## 4. Suggested Implementation Flow
1. **Create a dedicated monitoring role**
```sql
CREATE ROLE monitoring_user WITH LOGIN PASSWORD 'Strong!Passw0rd';
GRANT SELECT ON transactions TO monitoring_user;
GRANT SELECT ON mv_daily_totals TO monitoring_user; -- if using MV
```
2. **Schedule the job** (e.g., cron + `psql` or a DB‑native scheduler)
```bash
0 2 * * * psql -U monitoring_user -d prod_db -c "
SELECT user_id,
COUNT(*) AS transaction_count,
SUM(amount) AS total_amount
FROM transactions
WHERE created_at > NOW() - INTERVAL '1 DAY'
GROUP BY user_id
HAVING SUM(amount) > 10000;
" > /secure/monitoring/suspicious_activity_$(date +%F).csv
```
3. **Encrypt the output file**
```bash
gpg --encrypt --recipient monitoring_team@example.com \
/secure/monitoring/suspicious_activity_$(date +%F).csv
```
4. **Log the run** (audit table)
```sql
INSERT INTO audit_log (run_at, job_name, rows_returned)
VALUES (NOW(), 'daily_suspicious_activity', (SELECT COUNT(*) FROM ...));
```
5. **Alert**
- If `rows_returned > 0`, push a message to your SIEM or Slack channel.
- If `rows_returned > 10`, trigger a higher‑level escalation.
---
## 5. Quick‑Check Summary
| ✅ | Item |
|----|------|
| ✅ | Run on read‑replica / off‑peak |
| ✅ | Composite index on `(created_at, user_id, amount)` |
| ✅ | Use deterministic timestamp or parameter |
| ✅ | Avoid alias in `HAVING` |
| ✅ | Encrypt data in transit & at rest |
| ✅ | Apply RLS & audit logging |
| ✅ | HA, backup, DR |
| ✅ | Monitoring & alerting |
| ✅ | Secure output & retention policy |
---
### Final Thought
Your query is *functionally correct* for spotting high‑value daily activity, but in a healthcare setting you must treat the result set as PHI and enforce the full HIPAA compliance stack around it. By following the checklist above, you’ll keep the system **secure, auditable, and performant**—exactly what a life‑supporting environment demands.[0m
----------------------------------------
================================================================================
=== DETAILED PERSONA ANALYSIS ===
Query: SELECT * FROM user_activity WHERE session_duration > 3600
Context: Analyzing user engagement patterns
============================================================
--- ALEX CHEN (Senior Data Engineer) ---
[94m**Quick Take‑away**
- **Don’t use `SELECT *`** – it forces the engine to read every column, which can be expensive for a large `user_activity` table.
- **Add a covering index** on `(session_duration)` (and any columns you actually need).
- **Partition by date** (or user ID) to reduce the scan volume.
- **Consider a materialized view** or pre‑aggregated table if you run this query often.
- **Monitor cardinality** – if only a few rows match, a simple index will be enough; if many rows match, you’ll need a more selective filter or a different storage strategy.
---
## 1. Why `SELECT *` is a problem
| Issue | Impact |
|-------|--------|
| Reads all columns | Increases I/O, memory usage, and network traffic. |
| Skips column pruning | Even if you only need a few fields, the engine still fetches the rest. |
| Can break schema changes | Adding a new column forces the query to re‑evaluate the whole table. |
**Recommendation**: Explicitly list the columns you need, e.g.:
```sql
SELECT user_id,
session_start,
session_end,
session_duration,
device_type
FROM user_activity
WHERE session_duration > 3600;
```
---
## 2. Indexing strategy
### 2.1. Simple B‑Tree index
If `session_duration` is a numeric field and you rarely query by other columns:
```sql
CREATE INDEX idx_user_activity_session_duration
ON user_activity (session_duration);
```
**Pros**
- Fast look‑ups for the > 3600 filter.
- Low maintenance cost.
**Cons**
- Still scans all columns unless the query is *covering* (see below).
### 2.2. Covering index
Add the columns you actually need to the index:
```sql
CREATE INDEX idx_user_activity_long_sessions
ON user_activity (session_duration)
INCLUDE (user_id, session_start, session_end, device_type);
```
Now the query can be satisfied entirely from the index, avoiding a heap scan.
**When to use**
- When the table is large (> 100M rows).
- When the query is run frequently.
---
## 3. Partitioning
If your table is time‑based (common for activity logs), partition by month or week:
```sql
CREATE TABLE user_activity (
user_id BIGINT,
session_start TIMESTAMP,
session_end TIMESTAMP,
session_duration INT,
device_type VARCHAR(32),
...
) PARTITION BY RANGE (session_start);
-- Example partitions
CREATE TABLE user_activity_2025_07 PARTITION OF user_activity
FOR VALUES FROM ('2025-07-01') TO ('2025-08-01');
```
**Benefits**
- Query planner can prune entire partitions that cannot contain long sessions.
- Maintenance (vacuum, analyze, drop old partitions) is easier.
**Caveat**
- Partition key must be part of the query filter or used in the index to be effective.
---
## 4. Materialized view (if query is ad‑hoc)
If you need to run this query daily (or more often) and the result set is relatively stable:
```sql
CREATE MATERIALIZED VIEW mv_long_sessions AS
SELECT user_id,
session_start,
session_end,
session_duration,
device_type
FROM user_activity
WHERE session_duration > 3600;
```
Refresh it incrementally:
```sql
REFRESH MATERIALIZED VIEW CONCURRENTLY mv_long_sessions;
```
**Pros**
- Near‑instant query response.
- Offloads heavy scanning to a scheduled job.
**Cons**
- Requires storage space.
- Needs a refresh strategy that balances freshness vs. cost.
---
## 5. Cost‑aware execution
1. **Explain plan** – always run `EXPLAIN (ANALYZE, BUFFERS)` on the query to see if the index is used and how many rows are scanned.
2. **Monitor I/O** – high buffer reads indicate a full table scan.
3. **Adjust autovacuum** – ensure statistics are up‑to‑date so the planner picks the right plan.
---
## 6. Conservative production change checklist
| Step | Action | Why |
|------|--------|-----|
| 1 | Test the query on a staging copy | Avoid unintentional downtime. |
| 2 | Run `EXPLAIN` before and after index/partition changes | Verify performance gains. |
| 3 | Deploy index in a rolling fashion (e.g., create index concurrently) | Minimize lock contention. |
| 4 | Add monitoring alerts for query latency > threshold | Catch regressions early. |
| 5 | Document changes in the data‑engineering wiki | Ensure knowledge transfer. |
---
## 7. Final recommendation
1. **Rewrite the query** to select only needed columns.
2. **Create a covering index** on `(session_duration)` with the included columns you actually query.
3. **If the table is time‑partitioned**, ensure the partition key is part of the filter or the index.
4. **Run an explain plan** to confirm the index is used and that the plan is efficient.
5. **If the query is frequent**, consider a materialized view or a dedicated “long sessions” table that is refreshed nightly.
This approach keeps the change small, low risk, and scalable as the data grows.[0m
----------------------------------------
--- MORGAN TAYLOR (Lead Security Engineer) ---
[94m**Morgan Taylor – Lead Security Engineer, SecureFinance**
---
### 1. Immediate Security & Compliance Assessment
| Concern | Observation | Recommendation |
|---------|-------------|----------------|
| **Data Exposure** | `SELECT *` pulls **every** column from `user_activity`. If the table contains PII (e.g., `user_id`, `email`, `device_id`) or sensitive telemetry, this is a *data minimization* violation under GDPR/CCPA. | Enumerate only the columns you actually need (e.g., `user_id, session_start, session_end, session_duration`). |
| **Least‑Privilege Principle** | The query is being run by an analyst or BI tool. If the executing role has `SELECT *` on the entire table, that role may have more access than required. | Create a dedicated read‑only role with `SELECT` on the *specific columns* needed. |
| **Audit Trail** | No mention of logging. | Ensure the DB audit log captures: <br>• Who ran the query (user/role) <br>• Timestamp <br>• Exact query text <br>• Result size (row count) |
| **Data Retention & Deletion** | The query could surface long‑running sessions that may be older than the retention window. | Verify that the query respects the data‑retention policy (e.g., filter by `session_start >= NOW() - INTERVAL '90 days'`). |
| **Performance & Resource Impact** | `SELECT *` on a potentially large table can be heavy. | Use indexes on `session_duration` and consider pagination or a `LIMIT` clause if you only need a sample. |
| **Injection Risk** | The query is static, so no injection risk here. | If this query is constructed dynamically in application code, use parameterized statements. |
| **Encryption** | Not specified. | Ensure encryption at rest (AES‑256) and TLS for data in transit. |
| **Compliance** | If the organization is subject to PCI, SOC 2, or other frameworks, data handling must be documented. | Document the purpose of the query, data classification, and mitigation steps. |
---
### 2. Clarifying Questions (to refine the assessment)
1. **Schema Details**
- What columns exist in `user_activity`?
- Which columns contain PII or sensitive telemetry?
2. **Data Classification**
- How is the data classified (Public, Internal, Confidential, Restricted)?
3. **User & Role Permissions**
- Which role is executing this query?
- Does that role have any `INSERT/UPDATE/DELETE` permissions on `user_activity`?
4. **Audit & Logging**
- Are audit logs enabled on the database?
- How long are audit logs retained?
5. **Retention Policy**
- What is the legal or business retention period for session data?
- Are there any legal constraints on accessing older sessions?
6. **Performance**
- Approximate size of `user_activity` (rows, storage).
- Is there an index on `session_duration`?
7. **Use Case**
- What specific engagement metrics are you after?
- Do you need raw rows or aggregated statistics?
8. **Data Masking / Anonymization**
- Are you required to mask or pseudonymize `user_id` in the output?
---
### 3. Suggested Revised Query
Assuming you only need user identifiers and session timestamps for engagement analysis, and that `user_id` is PII:
```sql
-- Run as a read‑only role with minimal privileges
SELECT
user_id,
session_start,
session_end,
session_duration
FROM
user_activity
WHERE
session_duration > 3600
AND session_start >= NOW() - INTERVAL '90 days' -- enforce retention
ORDER BY
session_start DESC
LIMIT 1000; -- adjust or remove if full result set is required
```
**Why this is safer:**
- **Column Whitelisting** – only pulls columns you explicitly need.
- **Retention Filter** – prevents accidental access to data older than the policy allows.
- **Ordering & Pagination** – reduces the risk of a runaway query that returns millions of rows.
- **Read‑Only Role** – ensures the executing user cannot modify data.
If you truly need *all* columns for a deeper forensic investigation, consider:
1. **Creating a temporary, read‑only view** that masks PII.
2. **Using a job scheduler** that runs under a dedicated service account with audit logging.
---
### 4. Operational Controls
| Control | Implementation |
|---------|----------------|
| **Role‑Based Access Control (RBAC)** | Create a `read_engagement` role with `SELECT` on the whitelisted columns only. |
| **Audit Logging** | Enable `pg_audit` (PostgreSQL) or equivalent, log all `SELECT` statements. |
| **Encryption** | Ensure `pgcrypto` or database‑level encryption is active. |
| **Monitoring** | Set up alerts for unusually large result sets or queries that run outside business hours. |
| **Data Masking** | Use column‑level masking or view‑level pseudonymization for PII. |
| **Retention Enforcement** | Automate deletion or archival of sessions older than the retention window. |
---
### 5. Final Thoughts
- **Security First**: Even a seemingly innocuous query can expose sensitive data if not properly scoped.
- **Compliance**: GDPR/CCPA demand *data minimization* and *purpose limitation*. `SELECT *` is a red flag.
- **Audit**: Every query that touches PII must be logged and reviewed.
- **Performance**: Large tables can exhaust resources; always index and paginate.
If you can share the answers to the clarifying questions above, I can provide a more tailored risk assessment and remediation plan.[0m
----------------------------------------
Constraint-Based Prompting: Setting Boundaries That Work
Want consistent outputs? Don't ask nicely or do begging (😆). Set hard constraints.
def generate_migration_script(changes: dict) -> str:
"""Generate database migration with strict constraints"""
constraints = """
HARD CONSTRAINTS (MUST follow):
- Use transactions for all DDL operations
- Include rollback statements
- Add IF EXISTS checks
- Maximum 5 operations per transaction
- Include timing estimates as comments
FORBIDDEN:
- Direct table drops without backups
- Changing primary keys
- Removing columns without deprecation notice
"""
prompt = f"""
Generate a migration script for these changes:
{json.dumps(changes, indent=2)}
{constraints}
Output format: Valid SQL with comments
"""
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{"role": "system", "content": "You are a database migration expert. Safety is paramount."},
{"role": "user", "content": prompt}
],
temperature=0.1 # Low temperature for consistency
)
return response["choices"][0]["message"]["content"]
Run this example yourself 🔧
Script:
5_constraint_based_prompting.py
Command:
uv run 5_constraint_based_prompting.pyExpected Output:
Constraint-Based Prompting Demo
=== CONSTRAINT ADHERENCE TEST ===
--- Migration Script Generation ---
Generated Migration:
[94m```sql
-- =========================================================
-- Migration: Add user_preferences table, columns, and index
-- Author: <Your Name>
-- Date: 2025-08-16
-- =========================================================
-- ==============================
-- Transaction 1: Create table
-- Estimated time: 0.10 s
-- ==============================
BEGIN;
CREATE TABLE IF NOT EXISTS user_preferences (
user_id BIGINT PRIMARY KEY,
theme VARCHAR(50),
notification_settings JSONB
);
COMMIT;
-- ==============================
-- Transaction 2: Add column "theme"
-- Estimated time: 0.05 s
-- ==============================
BEGIN;
ALTER TABLE user_preferences
ADD COLUMN IF NOT EXISTS theme VARCHAR(50);
COMMIT;
-- ==============================
-- Transaction 3: Add column "notification_settings"
-- Estimated time: 0.05 s
-- ==============================
BEGIN;
ALTER TABLE user_preferences
ADD COLUMN IF NOT EXISTS notification_settings JSONB;
COMMIT;
-- ==============================
-- Transaction 4: Create index
-- Estimated time: 0.05 s
-- ==============================
BEGIN;
CREATE INDEX IF NOT EXISTS idx_user_preferences_user_id
ON user_preferences(user_id);
COMMIT;
-- =========================================================
-- Rollback script (to revert the migration)
-- Estimated time: 0.20 s
-- =========================================================
BEGIN;
-- Drop index if it exists
DROP INDEX IF EXISTS idx_user_preferences_user_id;
-- Drop columns if they exist
ALTER TABLE user_preferences DROP COLUMN IF EXISTS theme;
ALTER TABLE user_preferences DROP COLUMN IF EXISTS notification_settings;
-- Backup the table before dropping it
CREATE TABLE backup_user_preferences AS TABLE user_preferences;
-- Drop the table if it exists
DROP TABLE IF EXISTS user_preferences;
COMMIT;
```[0m
--------------------------------------------------
--- Security Constrained Generator ---
Request: Find users by email address
Generated Query:
[94m-- SQL Injection Prevention: Use parameterized query with placeholder $1
-- Input validation should be performed in the application layer (e.g., regex for email format)
WITH audit_log AS (
INSERT INTO user_access_audit (
user_id,
access_time,
accessed_by,
query_type
)
VALUES (
NULL, -- NULL indicates system-initiated audit
CURRENT_TIMESTAMP,
'admin', -- user_role from context
'SELECT_BY_EMAIL'
)
RETURNING audit_id
)
SELECT
u.id,
u.name,
CONCAT(LEFT(u.email, 3), '****', RIGHT(u.email, 4)) AS masked_email,
u.created_at,
a.audit_id
FROM
users u
JOIN audit_log a ON 1=1
/*+ INDEX(u idx_users_email) */ -- Hint to use index on email column
WHERE
u.email = $1
LIMIT 100; -- Respect max_results from context
/* Data retention policy: audit records older than 90 days are purged by a scheduled job. */
[0m
Request: Get user login history
Generated Query:
[94m```sql
CREATE PROCEDURE dbo.GetUserLoginHistory
@UserId INT,
@StartDate DATETIME,
@EndDate DATETIME
AS
BEGIN
SET NOCOUNT ON;
/*--------------------------------------------------------------
* SQL Injection Prevention:
* - Only parameterized queries are used.
* - No dynamic SQL or string concatenation in WHERE clauses.
*--------------------------------------------------------------*/
/* Validate input parameters */
IF @UserId IS NULL OR @StartDate IS NULL OR @EndDate IS NULL
BEGIN
RAISERROR('Invalid input parameters', 16, 1);
RETURN;
END
IF @StartDate > @EndDate
BEGIN
RAISERROR('StartDate must be less than or equal to EndDate', 16, 1);
RETURN;
END
/* Log data access attempt (audit trail) */
INSERT INTO dbo.audit_log (user_id, action, action_timestamp, ip_address)
VALUES (@UserId,
'GetUserLoginHistory',
GETDATE(),
CONNECTIONPROPERTY('client_net_address'));
/* Retrieve login history with masking and retention filter */
SELECT TOP (100)
lh.user_id,
lh.login_time,
CONCAT(
SUBSTRING(lh.ip_address,
1,
CHARINDEX('.', lh.ip_address, CHARINDEX('.', lh.ip_address)+1)-1),
'.***.***') AS masked_ip,
lh.device,
lh.location
FROM dbo.login_history lh WITH (INDEX(idx_user_login_time))
WHERE lh.user_id = @UserId
AND lh.login_time BETWEEN @StartDate AND @EndDate
AND lh.login_time >= DATEADD(day, -365, GETDATE()) -- retention policy
ORDER BY lh.login_time DESC;
END
```[0m
--------------------------------------------------
--- Performance Constrained Generator ---
Request: Get top selling products
Generated Query:
[94m```sql
/* TAG: top_selling_products
ESTIMATED_ROWS: 5000
LOG_SLOW_QUERY
Execution plan: (will be generated by the optimizer)
/*+ READ_REPLICA MAX_EXECUTION_TIME(30000) INDEX(sales sales_product_id_idx) INDEX(products products_product_id_idx) */
SELECT
p.product_id,
p.product_name,
SUM(s.quantity) AS total_quantity
FROM
sales /*+ INDEX(sales sales_product_id_idx) */ s
JOIN
products /*+ INDEX(products products_product_id_idx) */ p
ON s.product_id = p.product_id
WHERE
s.sale_date >= DATE_SUB(CURDATE(), INTERVAL 30 DAY)
GROUP BY
p.product_id,
p.product_name
ORDER BY
total_quantity DESC
LIMIT 1000;
```[0m
Request: Find customers with high order values
Generated Query:
[94m```sql
/* TAG: high_order_value_report
ESTIMATED ROWS: 500
LOG_SLOW_QUERY_WARNING
MAX_EXECUTION_TIME(30000) -- 30 seconds
READ_REPLICA
INDEX(orders idx_orders_customer_id_date_value)
*/
SELECT
c.customer_id,
c.customer_name,
SUM(o.order_value) AS total_order_value,
COUNT(o.order_id) AS order_count
FROM
customers c
JOIN
orders o
ON c.customer_id = o.customer_id
WHERE
o.order_date >= DATE_SUB(CURDATE(), INTERVAL 30 DAY)
AND o.order_value > 1000
GROUP BY
c.customer_id,
c.customer_name
ORDER BY
total_order_value DESC
LIMIT 1000;
/* Execution plan:
1. Use covering index idx_orders_customer_id_date_value on orders to filter by order_date and order_value.
2. Join customers using primary key on customer_id.
3. Aggregate results in memory (hash aggregation).
4. Sort by total_order_value and limit to 1000 rows.
*/
```[0m
Request: Generate monthly sales report
Generated Query:
[94m```sql
/* TAG: monthly_sales_report */
/* ESTIMATED ROWS: 200 */
/* LOG_SLOW_QUERY_WARNING */
/*+ READ_REPLICA MAX_EXECUTION_TIME(30000) */
/* Using covering index sales_idx_date_amount_product on sales(sale_date, amount, product_id) */
/* Using index products_idx_id on products(id) */
/* Using index customers_idx_id on customers(id) */
SELECT
DATE_TRUNC('month', s.sale_date) AS sale_month,
p.name AS product_name,
c.region AS customer_region,
SUM(s.amount) AS total_sales,
COUNT(*) AS sales_count
FROM
sales s
JOIN
products p ON s.product_id = p.id
JOIN
customers c ON s.customer_id = c.id
WHERE
s.sale_date >= CURRENT_DATE - INTERVAL '30 days'
GROUP BY
sale_month, p.name, c.region
ORDER BY
sale_month DESC
LIMIT 1000;
/* Execution Plan: (to be generated by optimizer) */
```[0m
================================================================================
=== CONSTRAINT ENFORCEMENT DEMO ===
Testing format constraints:
Request: Count active users
JSON Output:
[94m{
"query": "-- type: count\nSELECT COUNT(*) FROM users WHERE status = 'active';",
"explanation": "Counts all users marked as active.",
"estimated_cost": "low",
"confidence": 0.95
}[0m
✓ Valid JSON format
Request: Find expensive orders
JSON Output:
[94m{
"query": "-- type: select\nSELECT * FROM orders WHERE total_amount > 1000;",
"explanation": "Select orders with total_amount greater than 1000",
"estimated_cost": "low",
"confidence": 0.95
}[0m
✓ Valid JSON format
Request: List product categories
JSON Output:
[94m{
"query": "-- query: list product categories\nSELECT DISTINCT category\nFROM products;\n",
"explanation": "Retrieves distinct product categories from the products table.",
"estimated_cost": "low",
"confidence": 0.95
}[0m
✓ Valid JSON format
================================================================================
=== BOUNDARY CONDITIONS TEST ===
Challenging request: Search all text fields for any mention of a user-provided term
Response:
[94m```sql
-- Assumes a full‑text index exists on (Column1, Column2, Column3) in dbo.MyTable
CREATE PROCEDURE dbo.SearchAllTextFields
@searchTerm NVARCHAR(4000) -- validated by the caller
AS
BEGIN
SET NOCOUNT ON;
SELECT *
FROM dbo.MyTable
WHERE CONTAINS((Column1, Column2, Column3), @searchTerm);
END;
```[0m
----------------------------------------
Challenging request: Generate a dynamic report with user-defined columns and filters
Response:
[94m```sql
-- Assumes a composite covering index named idx_All on (Col1, Col2, Col3)
CREATE PROCEDURE dbo.GetDynamicReport
@IncludeCol1 BIT = 0,
@IncludeCol2 BIT = 0,
@IncludeCol3 BIT = 0,
@FilterCol1 INT = NULL,
@FilterCol2 VARCHAR(50) = NULL,
@FilterCol3 DATE = NULL
AS
BEGIN
SET NOCOUNT ON;
SELECT
CASE WHEN @IncludeCol1 = 1 THEN t.Col1 END AS Col1,
CASE WHEN @IncludeCol2 = 1 THEN t.Col2 END AS Col2,
CASE WHEN @IncludeCol3 = 1 THEN t.Col3 END AS Col3
FROM dbo.MyTable t
WITH (INDEX(idx_All))
WHERE (@FilterCol1 IS NULL OR t.Col1 = @FilterCol1)
AND (@FilterCol2 IS NULL OR t.Col2 = @FilterCol2)
AND (@FilterCol3 IS NULL OR t.Col3 = @FilterCol3);
END
```[0m
----------------------------------------
Challenging request: Find similar records using fuzzy matching across all tables
Response:
[94m```sql
-- Assumes full‑text indexes exist on the searched columns
SELECT 'customers' AS source_table, id, name
FROM customers
WHERE CONTAINS(name, @searchTerm)
UNION ALL
SELECT 'orders' AS source_table, id, order_number
FROM orders
WHERE CONTAINS(order_number, @searchTerm)
UNION ALL
SELECT 'products' AS source_table, id, product_name
FROM products
WHERE CONTAINS(product_name, @searchTerm);
```
[0m
----------------------------------------
Output Formatting: Force Structure from the Start
Stop parsing messy LLM outputs. Force structured responses from the beginning.
import json
def extract_structured_data(text: str, schema: dict) -> dict:
"""Extract structured data with guaranteed format"""
format_prompt = f"""
Extract information and return ONLY valid JSON matching this schema:
Schema: {json.dumps(schema, indent=2)}
Text: {text}
Rules:
- Return ONLY the JSON object, no explanation
- Use null for missing values
- Validate types match the schema
"""
response = completion(
model="openrouter/openai/gpt-oss-20b:free",
api_key=getenv("OPENROUTER_API_KEY"),
messages=[
{
"role": "system",
"content": "You are a JSON extraction expert. Output only valid JSON."
},
{"role": "user", "content": format_prompt}
],
temperature=0 # Zero temperature for deterministic output
)
return json.loads(response["choices"][0]["message"]["content"])
# Example usage
schema = {
"tables": ["list of table names"],
"operations": ["list of SQL operations"],
"complexity": "low|medium|high",
"estimated_runtime": "seconds as integer"
}
query_text = "This query joins users with orders and filters by date"
result = extract_structured_data(query_text, schema)
# Output: {"tables": ["users", "orders"], "operations": ["JOIN", "WHERE"], ...}
Run this example yourself 🔧
Script:
6_structured_output.py
Command:
uv run 6_structured_output.pyExpected Output:
Structured Output Demo
=== BASIC EXTRACTION ===
Input: This query joins users with orders and filters by date, grouping results by region
Extracted:
[94m{
"tables": [
"users",
"orders"
],
"operations": [
"join",
"filter",
"group by"
],
"complexity": "medium",
"estimated_runtime": 5
}[0m
================================================================================
=== STRUCTURED QUERY ANALYSIS ===
--- Analysis 1 ---
Query: SELECT u.name, COUNT(o.id) as order_count, SUM(o.total) as total_spent
FROM users u
LEFT JOIN orders o ON u.id = o.user_id
WHERE u.created_at > '2024-01-01'
GROUP BY u.id
HAVING order_count > 5
ORDER BY total_spent DESC
Analysis:
[94m{
"tables": [
"users",
"orders"
],
"operations": [
"SELECT",
"LEFT JOIN",
"WHERE",
"GROUP BY",
"HAVING",
"ORDER BY",
"COUNT",
"SUM"
],
"complexity": "medium",
"estimated_runtime": 2,
"potential_issues": [
"Missing indexes on users.created_at, orders.user_id, and orders.total may slow query",
"LEFT JOIN is unnecessary since HAVING filters out users with no orders; could use INNER JOIN",
"SELECTing u.name without including it in GROUP BY may cause non-deterministic results in some SQL engines",
"SUM(o.total) will be NULL if all joined orders are NULL; consider COALESCE",
"Date literal '2024-01-01' may be affected by timezone settings"
],
"optimization_suggestions": [
"Replace LEFT JOIN with INNER JOIN to avoid unnecessary null handling",
"Add indexes on users.created_at, orders.user_id, and orders.total to speed up filtering and aggregation",
"Use COUNT(*) instead of COUNT(o.id) for slightly better performance",
"Consider pre-aggregating orders in a subquery to reduce data processed in GROUP BY",
"Use COALESCE(SUM(o.total),0) if NULL totals should be treated as zero"
],
"confidence_score": 0.95
}[0m
--- Analysis 2 ---
Query: SELECT * FROM products p, categories c, orders o, order_items oi
WHERE p.category_id = c.id
AND oi.product_id = p.id
AND oi.order_id = o.id
Analysis:
[94m{
"tables": [
"products",
"categories",
"orders",
"order_items"
],
"operations": [
"SELECT",
"FROM",
"WHERE"
],
"complexity": "low",
"estimated_runtime": 1,
"potential_issues": [
"Uses implicit join syntax which can be error\u2011prone",
"SELECT * returns all columns, causing unnecessary data transfer and possible column name collisions",
"No filtering or LIMIT clause, may return a very large result set",
"Missing indexes on foreign key columns (products.category_id, order_items.product_id, order_items.order_id) and primary keys",
"No explicit JOIN syntax, making join order unclear to optimizer",
"No use of specific columns, leading to heavier I/O"
],
"optimization_suggestions": [
"Rewrite using explicit JOIN syntax (INNER JOIN) for clarity",
"Add indexes on products.category_id, order_items.product_id, order_items.order_id, and primary keys of referenced tables",
"Select only required columns instead of *",
"Add appropriate WHERE filters or LIMIT to reduce result size",
"Consider using EXISTS or IN if applicable",
"Use query hints or optimizer directives if supported",
"Ensure statistics are up to date for better join ordering"
],
"confidence_score": 0.9
}[0m
--- Analysis 3 ---
Query: SELECT user_id FROM sessions WHERE last_activity > NOW() - INTERVAL 1 HOUR
Analysis:
[94m{
"tables": [
"sessions"
],
"operations": [
"SELECT",
"WHERE"
],
"complexity": "low",
"estimated_runtime": 1,
"potential_issues": [
"Potential full table scan if last_activity is not indexed",
"No LIMIT clause may return large result set",
"No index on last_activity may degrade performance"
],
"optimization_suggestions": [
"Add index on last_activity",
"Add LIMIT clause if only a subset needed",
"Use covering index on user_id and last_activity",
"Consider partitioning sessions table by activity date"
],
"confidence_score": 0.99
}[0m
================================================================================
=== STRUCTURED SECURITY AUDIT ===
--- Security Audit 1 ---
Query: SELECT * FROM users WHERE username = 'user_input'
Security Audit:
[94m{
"vulnerability_level": "high",
"vulnerabilities_found": [
"SQL Injection",
"Data Exposure"
],
"sql_injection_risk": true,
"data_exposure_risk": true,
"recommendations": [
"Use parameterized queries or prepared statements to avoid direct string concatenation.",
"Specify only required columns instead of SELECT * to limit data exposure.",
"Implement input validation and sanitization for user_input.",
"Apply least privilege principle on database user permissions."
],
"compliant_with_standards": [],
"audit_score": "2"
}[0m
--- Security Audit 2 ---
Query: SELECT * FROM credit_cards WHERE user_id = 123
Security Audit:
[94m{
"vulnerability_level": "medium",
"vulnerabilities_found": [
"SELECT * may expose unnecessary sensitive data"
],
"sql_injection_risk": false,
"data_exposure_risk": true,
"recommendations": [
"Specify only required columns instead of SELECT *",
"Use parameterized queries to prevent injection",
"Apply least privilege principle for database user",
"Encrypt sensitive data at rest",
"Implement proper access controls and logging"
],
"compliant_with_standards": [
"PCI-DSS",
"OWASP Top 10"
],
"audit_score": 6
}[0m
--- Security Audit 3 ---
Query: SELECT password_hash, salt FROM users WHERE email = ?
Security Audit:
[94m{
"vulnerability_level": "medium",
"vulnerabilities_found": [
"Retrieval of password_hash and salt may expose sensitive data if not properly protected",
"Potential data exposure if query results are returned to client",
"No explicit access control or rate limiting shown"
],
"sql_injection_risk": false,
"data_exposure_risk": true,
"recommendations": [
"Avoid returning password_hash and salt to client; store them securely",
"Use strong hashing algorithm with salt (e.g., bcrypt, Argon2)",
"Ensure database credentials have least privilege",
"Implement proper access controls and audit logging",
"Apply rate limiting to prevent enumeration attacks",
"Encrypt sensitive data at rest",
"Use parameterized queries (already in place) to mitigate SQL injection"
],
"compliant_with_standards": [
"OWASP Secure Coding Practices",
"PCI-DSS (partial compliance)"
],
"audit_score": 6
}[0m
--- Security Audit 4 ---
Query: UPDATE users SET admin = 1 WHERE user_id = user_controlled_id
Security Audit:
[94m{
"vulnerability_level": "high",
"vulnerabilities_found": [
"SQL injection",
"Privilege escalation via unsanitized user_id",
"Missing parameterization"
],
"sql_injection_risk": true,
"data_exposure_risk": true,
"recommendations": [
"Use parameterized queries or prepared statements",
"Validate and sanitize user_id input",
"Implement least privilege and role-based access control",
"Add audit logging for privilege changes",
"Consider using stored procedures",
"Enforce input validation and type checking"
],
"compliant_with_standards": [],
"audit_score": 2
}[0m
================================================================================
=== STRUCTURED PERFORMANCE REPORT ===
--- Performance Report 1 ---
Query: SELECT COUNT(*) FROM orders o
JOIN order_items oi ON o.id = oi.order_id
JOIN products p ON oi.product_id = p.id
WHERE o.created_at > '2023-01-01'
Performance Report:
[94m{
"estimated_execution_time": "5-10 seconds",
"resource_usage": {
"cpu_intensive": false,
"memory_intensive": false,
"io_intensive": true
},
"scalability_concerns": [
"Large number of rows in orders and order_items leading to join amplification",
"Potential full table scans if indexes missing",
"High I/O load on disk for scanning and joining",
"Counting after join may become expensive as data grows"
],
"recommended_indexes": [
"CREATE INDEX idx_orders_created_at ON orders(created_at);",
"CREATE INDEX idx_order_items_order_id ON order_items(order_id);",
"CREATE INDEX idx_order_items_product_id ON order_items(product_id);",
"CREATE INDEX idx_products_id ON products(id);"
],
"alternative_approaches": [
"SELECT COUNT(*) FROM order_items oi JOIN orders o ON oi.order_id = o.id WHERE o.created_at > '2023-01-01';",
"Use a derived table: SELECT COUNT(*) FROM (SELECT oi.id FROM order_items oi JOIN orders o ON oi.order_id = o.id WHERE o.created_at > '2023-01-01') AS sub;",
"Create a materialized view that pre-aggregates counts per order date and query that view instead of joining large tables;"
],
"bottlenecks": [
"Join amplification due to many order_items per order",
"Missing indexes causing full table scans",
"Counting after join forces processing of all joined rows"
],
"optimization_priority": "high"
}[0m
--- Performance Report 2 ---
Query: SELECT u.*,
(SELECT COUNT(*) FROM orders WHERE user_id = u.id) as order_count,
(SELECT SUM(total) FROM orders WHERE user_id = u.id) as total_spent
FROM users u
Performance Report:
[94m{
"estimated_execution_time": "10 seconds",
"resource_usage": {
"cpu_intensive": false,
"memory_intensive": false,
"io_intensive": true
},
"scalability_concerns": [
"High I/O due to correlated subqueries",
"Scales poorly with large user and order tables",
"Potential for long query times as data grows"
],
"recommended_indexes": [
"CREATE INDEX idx_orders_user_id ON orders(user_id);",
"CREATE INDEX idx_orders_user_id_total ON orders(user_id, total);"
],
"alternative_approaches": [
"SELECT u.*, o.order_count, o.total_spent FROM users u LEFT JOIN (SELECT user_id, COUNT(*) AS order_count, SUM(total) AS total_spent FROM orders GROUP BY user_id) o ON u.id = o.user_id;",
"Use window functions: SELECT u.*, COUNT(*) OVER (PARTITION BY u.id) AS order_count, SUM(total) OVER (PARTITION BY u.id) AS total_spent FROM users u LEFT JOIN orders ON orders.user_id = u.id;",
"Materialize aggregates in a separate table and update via triggers."
],
"bottlenecks": [
"Correlated subqueries causing repeated scans of orders table",
"Missing index on orders.user_id",
"Potential full table scans for each user"
],
"optimization_priority": "high"
}[0m
--- Performance Report 3 ---
Query: SELECT * FROM logs
WHERE message LIKE '%error%'
AND created_at BETWEEN '2024-01-01' AND '2024-12-31'
ORDER BY created_at DESC
Performance Report:
[94m{
"estimated_execution_time": "5-10 seconds",
"resource_usage": {
"cpu_intensive": false,
"memory_intensive": false,
"io_intensive": true
},
"scalability_concerns": [
"Full table scans on large logs table",
"High I/O load due to leading wildcard in LIKE",
"Potential lock contention on ORDER BY",
"Index fragmentation over time"
],
"recommended_indexes": [
"CREATE INDEX idx_logs_created_at ON logs(created_at DESC);",
"CREATE FULLTEXT INDEX idx_logs_message_ft ON logs(message);",
"CREATE INDEX idx_logs_created_at_message ON logs(created_at, message);"
],
"alternative_approaches": [
"Use full-text search instead of LIKE",
"Partition logs table by year to reduce scan size",
"Create a materialized view for error logs",
"Add a computed boolean column is_error and index it"
],
"bottlenecks": [
"Leading wildcard in LIKE prevents index usage",
"Large volume of log rows",
"Sorting on created_at after filtering"
],
"optimization_priority": "high"
}[0m
================================================================================
=== EDGE CASES TEST ===
--- Edge Case 1 ---
Input: 'Analyze this completely invalid SQL: SELECT * FROM nowhere WHERE nothing = everything'
Response:
[94m{
"status": "error",
"message": "Invalid SQL query: SELECT * FROM nowhere WHERE nothing = everything",
"data": null
}[0m
--- Edge Case 2 ---
Input: 'What is the meaning of life?'
Response:
[94m{
"status": "success",
"message": "Answer to the meaning of life.",
"data": "The meaning of life is to seek purpose, connection growth."
}[0m
--- Edge Case 3 ---
Input: 'Generate a SQL query for something impossible'
Response:
[94m{
"status": "error",
"message": "Cannot generate a SQL query for an impossible task.",
"data": null
}[0m
--- Edge Case 4 ---
Input: ''
Response:
[94m{
"status": "success",
"message": "No input provided",
"data": null
}[0m
Key Takeaways
- Context beats cleverness — A clear system prompt with specific constraints outperforms fancy prompting tricks every time
- Examples > explanations — Few-shot learning with 2-3 examples teaches patterns better than long descriptions
- Structure first, content second — Force JSON outputs and defined formats to avoid parsing nightmares
- Temperature matters — Use 0-0.2 for consistent outputs, 0.3-0.7 for creative tasks
- Chain-of-thought when it counts — For complex reasoning, make the model show its work
- Role definition depth — "Senior DBA with 15 years experience" gets better results than "SQL expert"
What's Next?
Ready to dive deeper? Let's explore how agents use these prompts to actually reason and make decisions...
Technical deep dive series — Part 1 of 5

Comments
Join the discussion! Your thoughts and feedback are valuable.
💡 Comments are powered by GitHub Discussions. You'll need a GitHub account to comment. Make sure Discussions are enabled in the repository.